from boeing.com: As a pilotless F-16 roared into the sky last week at Tyndall Air Force Base, Fla., members of Boeing’s QF-16 team and the U.S. Air Force celebrated.
The flight represented the first unmanned QF-16 Full Scale Aerial Target flight. Put another way, fighter pilots now have an adversary for which to train against that prepares them like never before.
Two U.S. Air Force test pilots in a ground control station at Tydall remotely flew the QF-16, which is a retired F-16 jet modified to be an aerial target. While in the air, the QF-16 mission included a series of simulated maneuvers, reaching supersonic speeds, returning to base and landing, all without a pilot in the cockpit.
“It was a little different to see it without anyone in it, but it was a great flight all the way around,” said U.S. Air Force Lt. Col. Ryan Inman, Commander, 82nd Aerial Targets Squadron. “It’s a replication of current, real world situations and aircraft platforms they can shoot as a target. Now we have a 9G capable, highly sustainable aerial target.”
Prior to the QF-16, the military used a QF-4 aircraft, which was a modification of the F-4 Phantom, a Vietnam-era fighter The modified QF-16 provides pilots a target that performs closer to many jets flying today.
The QF-16s were all retired aircraft. Boeing retrieved them from Davis Monthan Air Force Base in Arizona and restored them for flight.
Next up, live fire testing moves to Holloman Air Force Base, N.M. The military will ultimately use QF-16s for weapons testing and other aerial training. So far, Boeing has modified six F-16s into the QF-16 configuration.
Wednesday, September 25, 2013
#NSA accused of hacking into India's nuclear systems
from thehindu.com: The public assertions made by Indian and American officials that no content was taken from India’s internet and telephone networks by U.S.’s National Security Agency (NSA) and that the American surveillance programs just looked at “patterns of communication” as a counter-terrorism measure are far from the truth, if not outright misleading.
According to a top secret document disclosed by NSA whistleblower Edward Snowden and obtained by The Hindu, the PRISM programme was deployed by the American agency to gather key information from India by tapping directly into the servers of tech giants which provide services such as email, video sharing, voice-over-IPs, online chats, file transfer and social networking services.
And, according to the PRISM document seen by The Hindu, much of the communication targeted by the NSA is unrelated to terrorism, contrary to claims of Indian and American officials.
Instead, much of the surveillance was focused on India’s domestic politics and the country’s strategic and commercial interests.
This is the first time it’s being revealed that PRISM, which facilitates extensive, in-depth surveillance on live communications as well as stored information, was used by the world’s largest surveillance organization to intercept and pick content on at least three issues related to India’s geopolitical and economic interests. They are: Nuclear, Space and Politics.
The top-secret NSA document, which carries the seal of “Special Source Operations”, is called “A Week in the Life of PRISM reporting” and it shows “Sampling of Reporting topics from 2-8 Feb 2013”. Marked with a green slug that reads “589 End product Reports’’, the document carries the brand logos of companies like Gmail, Facebook, MSN, Hotmail, Yahoo!, Google, Apple, Skype, YouTube, paltalk.com and AOL on the top of the page.
“End products” are official reports that are distillations of the best raw intelligence.
In a section titled “India”, the document clearly mentions numerous subjects about which content was picked from various service providers on the worldwide web in just one week early this year.
This document is strong evidence of the fact that NSA surveillance in India was not restricted to tracking of phone calls, text messages and email logs by Boundless Informant, an NSA tool that was deployed quite aggressively against India. “As politics, space and nuclear are mentioned as “end products” in this document, it means that emails, texts and phones of important people related to these fields were constantly monitored and intelligence was taken from them, and then the NSA prepared official reports on the basis of raw intelligence. It means, they are listening in real time to what our political leaders, bureaucrats and scientists are communicating with each other,” an official with an India intelligence agency told The Hindu, speaking strictly on condition of anonymity.
But, top ministers and officials have continued to live in denial.
After it was reported by The Guardian on June 7 that the PRISM program allowed the NSA “to obtain targeted communications without having to request them from the service providers and without having to obtain individual court orders”, both U.S. and Indian officials claimed that no content was being taken from the country’s networks and that the programs were intended to “counter terrorism”.
Kerry’s dissembling
During his visit to New Delhi on June 24 to take part in the India-U.S. Strategic Dialogue, U.S. Secretary of State John Kerry denied that the American agency programmes were accessing online content. “It does not look at individual emails. It does not listen to people’s telephone conversation. It is a random survey by computers of anybody’s telephone, of just the numbers and not even the names…It takes those random numbers and looks whether those random numbers are connected to other numbers, that they know, by virtue of other intelligence, linked to terrorists in places where those terrorists operate,” Mr. Kerry had said, stressing that only when an “adequate linkage” is formed, the authorities go to a special court to get permission to obtain further data.
Even Indian officials have been repeating these lines since the NSA activities in India were disclosed. Replying to a question in Rajya Sabha on August 26, Communications and Information Technology Minister Kapil Sibal said the U.S. agencies only “trace origin and destination of the data, but never try to get access to the content, which requires a court approval”. “It would be a matter of concern for government if intrusive data capture has been deployed against Indian citizens or government infrastructure. Government has clearly conveyed these concerns to the U.S. government,” the minister had said, adding that the violation of any Indian law relating to privacy of information of ordinary Indian citizens by surveillance programs was “unacceptable”.
This “unacceptable” line might have been crossed by the NSA millions of times through the PRISM program as, according to the documents disclosed by Mr. Snowden, it is able to reach directly into the servers of the tech companies that are part of the programme and obtain data as well as perform real-time collection on targeted users. “The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other U.S. internet giants,” The Guardian had said in its June 7 report, quoting from a 41-slide PowerPoint presentation which was apparently used to train intelligence operatives on the capabilities of the program.
Foreigners are fair game
Tech firms have denied that they allow unfettered access to the NSA. In strongly worded denials of participation in any government surveillance program, they have claimed they allow access to any data to the agency only when required by law.
Here lies the catch. Contrary to denials by tech firms and claims by India’s communication minister that the U.S. agency “requires a court approval” to look into any online content, the NSA used the changes in U.S. surveillance law that allows for the targeting of any customers of participating firms “who live outside the US, or those Americans whose communications include people outside the US”. This law, known as FISA Amendment Act or FAA, was introduced by President George W Bush and renewed under President Barack Obama in December 2012, allows for electronic surveillance on anyone who is “reasonably believed” to be outside the U.S.
No Indian citizen, government department or organisation has any legal protection from NSA surveillance. In a Joint Statement from the Office of the Director of National Intelligence and the National Security Agency on August 21, 2013, it was stated that “FISA is designed to allow the U.S. Government to acquire foreign intelligence while protecting the civil liberties and privacy of Americans.”
So the NSA had no obstacle — technical or legal — in deploying the PRISM tool against India and Indian citizens. Armed with the FAA and with the active cooperation of the world’s biggest internet brands, the NSA was able to tap specific intelligence from India about the issues which have huge implications for its strategic interests in India. While India’s “nuclear” and “space” programmes have clearly significant commercial value for American firms, the surveillance of “politics” has huge implications for its foreign policy objectives in the region.
“If Americans are listening to our politicians and tapping the phones or reading mails of individuals who handle nuclear and space programmes, they have huge advantage over us in all business and diplomatic negotiations. Even before we go to the table, they know what we are going to put on it. It’s not just violation of our sovereignty, it’s a complete intrusion into our decision-making process,” said a senior official of the Ministry of Home Affairs, who admitted in private that the reports about the scale of NSA surveillance have “rattled” the government.
The NSA document also has names of several Asian, African and Latin American countries from where the American agency picked data about subjects ranging from oil to WTO to government policies, making it clear that the NSA spying was focused on commercial and business areas, and not on its stated objective of national security. “If the American intelligence agencies and business corporations are hunting in pairs, we are bound to lose,” added the Indian official.
More than anything, the targeting of India’s politics and space programme by the NSA busts the myth of close strategic partnership between India and US. The document seen by The Hindu is populated with the countries that are generally seen as adversarial by America. When the PRISM program was disclosed first time in June, a U.S. official had said that information “collected under this program is among the most important and valuable intelligence information we collect, and is used to protect our nation from a wide variety of threats.”
Labels:
boundless informant,
india,
nsa,
nuclear,
prism
Tuesday, September 24, 2013
World record solar cell with 44.7% efficiency
 |
| Credit: Fraunhofer ISE |
Back in May 2013, the German-French team of Fraunhofer ISE, Soitec, CEA-Leti and the Helmholtz Center Berlin had already announced a solar cell with 43.6% efficiency. Building on this result, further intensive research work and optimization steps led to the present efficiency of 44.7%.
These solar cells are used in concentrator photovoltaics (CPV), a technology which achieves more than twice the efficiency of conventional PV power plants in sun-rich locations. The terrestrial use of so-called III-V multi-junction solar cells, which originally came from space technology, has prevailed to realize highest efficiencies for the conversion of sunlight to electricity. In this multi-junction solar cell, several cells made out of different III-V semiconductor materials are stacked on top of each other. The single subcells absorb different wavelength ranges of the solar spectrum.
"We are incredibly proud of our team which has been working now for three years on this four-junction solar cell," says Frank Dimroth, Department Head and Project Leader in charge of this development work at Fraunhofer ISE. "This four-junction solar cell contains our collected expertise in this area over many years. Besides improved materials and optimization of the structure, a new procedure called wafer bonding plays a central role. With this technology, we are able to connect two semiconductor crystals, which otherwise cannot be grown on top of each other with high crystal quality. In this way we can produce the optimal semiconductor combination to create the highest efficiency solar cells."
"This world record increasing our efficiency level by more than 1 point in less than 4 months demonstrates the extreme potential of our four-junction solar cell design which relies on Soitec bonding techniques and expertise," says André-Jacques Auberton-Hervé, Soitec's Chairman and CEO. "It confirms the acceleration of the roadmap towards higher efficiencies which represents a key contributor to competitiveness of our own CPV systems. We are very proud of this achievement, a demonstration of a very successful collaboration."
"This new record value reinforces the credibility of the direct semiconductor bonding approaches that is developed in the frame of our collaboration with Soitec and Fraunhofer ISE. We are very proud of this new result, confirming the broad path that exists in solar technologies for advanced III-V semiconductor processing," said Leti CEO Laurent Malier.
Source: Phys.org
Is Outer Space the Sustainable Energy Solution?
from trueactivist.com: Sources of sustainable energy continue to be pursued with little to no avail; while well-thought out strategies are presented with good intention, it seems there’s always a fatal flaw that is uncovered. Solar power, hydro-power, nuclear, and wind power have all been dragged through the mud to some extent; ‘traditional nuclear fission is too risky, hydro-power dams disrupt the environment, the sun doesn’t penetrate through the clouds, and winds aren’t consistent’ are just a few of the arguments against the sustainability alternatives.
However, could the answer to achieving 100% pollution-free sustainable energy lie outside of the Earth’s atmosphere? The quest for extra-terrestrial sources of energy has brought to light many intriguing ideas (such as wind turbines on Mars), but one of the most realistic and best answers to solving the energy crisis relies in using helium-3, an Isotope of Helium, which is used to fuel the billions of stars in the universe.
One has to wonder how the sun burns in a void with no oxygen; the answer is that the reaction is different from combustion which takes place in Earth’s atmosphere. Instead, a reaction called nuclear fusion occurs where by the intense gravity forces four hydrogen atoms to fuse into one atom of helium. The resulted product weighs much less than the four hydrogen atoms, therefore the missing mass becomes a lot of energy. We observe this extra energy as light and heat, our sun. This phenomenon lends insight into why helium-3 could be an excellent source of energy on our planet.
As opposed to nuclear fission which splits an atom’s nucleus in half and poses potential risk due to radiation, nuclear fusion combines nuceli to produce energy. Nuclear fusion has already been tested with the hydrogen isotopes deuterium and tritium, but both reactions give off the majority of their heat as radioactive neutrons, a cause of safety and pollution concern. Helium-3, on the other hand, is perfectly safe, with no pollution or radioactive waste given off.
Helium-3 is an isotope of the element Helium; it has two protons but only one neutron. When it is heated to very high temperatures and combined with deuterium, the reactions releases incredible amounts of energy. In fact, just 2.2 pounds (1 kilo) of helium-3 combined with 1.5 pounds of deuterium produces 19 megawatt-years of energy. Roughly 25 pounds of the components could power the United States for an entire year.
The problem, however, lies in the sourcing of helium-3. While the United States is the largest supplier of Helium at 78% from what can be extracted from minerals and tapped gas deposits, the element only accounts for 0.00052% of the Earth’s atmosphere and therefore is not very abundant on this planet. Being the second lightest element and the second most abundant in the universe (24% of the cosmos), the solution is to look outside of our planetary borders.
The moon, for example, is estimated to contain over 1 million tons of Helium; the energy stored in that much Helium is 10 times the amount of energy you’d find in all of the fossil fuels on Earth. If one put a cash value on it, the helium-3 would be worth $4 billion a ton in terms of its energy equivalent in oil.
That said, the remaining issues rely in the practicality of extracting the Helium and fine-tuning the fusion process. Current fusion reactors have yet to achieve the sustained high temperatures needed to produce electricity, and helium-3 would require a lot of refining because it exists in such low concentrations in the soil. Another issue to consider is if the damage of emissions from rockets launched is worth the confiscating of Helium from the moon.
A large amount of risk is being invested to provide more energy, when perhaps the first goal should be to eradicate the excess usage caused by consumerist society and a lack of education. Regardless, if sustainable methods to extract and fuse the plentiful element are realized, the outlook for Earth’s sustainable future holds another alternative of hope.
However, could the answer to achieving 100% pollution-free sustainable energy lie outside of the Earth’s atmosphere? The quest for extra-terrestrial sources of energy has brought to light many intriguing ideas (such as wind turbines on Mars), but one of the most realistic and best answers to solving the energy crisis relies in using helium-3, an Isotope of Helium, which is used to fuel the billions of stars in the universe.
One has to wonder how the sun burns in a void with no oxygen; the answer is that the reaction is different from combustion which takes place in Earth’s atmosphere. Instead, a reaction called nuclear fusion occurs where by the intense gravity forces four hydrogen atoms to fuse into one atom of helium. The resulted product weighs much less than the four hydrogen atoms, therefore the missing mass becomes a lot of energy. We observe this extra energy as light and heat, our sun. This phenomenon lends insight into why helium-3 could be an excellent source of energy on our planet.
As opposed to nuclear fission which splits an atom’s nucleus in half and poses potential risk due to radiation, nuclear fusion combines nuceli to produce energy. Nuclear fusion has already been tested with the hydrogen isotopes deuterium and tritium, but both reactions give off the majority of their heat as radioactive neutrons, a cause of safety and pollution concern. Helium-3, on the other hand, is perfectly safe, with no pollution or radioactive waste given off.
Helium-3 is an isotope of the element Helium; it has two protons but only one neutron. When it is heated to very high temperatures and combined with deuterium, the reactions releases incredible amounts of energy. In fact, just 2.2 pounds (1 kilo) of helium-3 combined with 1.5 pounds of deuterium produces 19 megawatt-years of energy. Roughly 25 pounds of the components could power the United States for an entire year.
The problem, however, lies in the sourcing of helium-3. While the United States is the largest supplier of Helium at 78% from what can be extracted from minerals and tapped gas deposits, the element only accounts for 0.00052% of the Earth’s atmosphere and therefore is not very abundant on this planet. Being the second lightest element and the second most abundant in the universe (24% of the cosmos), the solution is to look outside of our planetary borders.
The moon, for example, is estimated to contain over 1 million tons of Helium; the energy stored in that much Helium is 10 times the amount of energy you’d find in all of the fossil fuels on Earth. If one put a cash value on it, the helium-3 would be worth $4 billion a ton in terms of its energy equivalent in oil.
That said, the remaining issues rely in the practicality of extracting the Helium and fine-tuning the fusion process. Current fusion reactors have yet to achieve the sustained high temperatures needed to produce electricity, and helium-3 would require a lot of refining because it exists in such low concentrations in the soil. Another issue to consider is if the damage of emissions from rockets launched is worth the confiscating of Helium from the moon.
A large amount of risk is being invested to provide more energy, when perhaps the first goal should be to eradicate the excess usage caused by consumerist society and a lack of education. Regardless, if sustainable methods to extract and fuse the plentiful element are realized, the outlook for Earth’s sustainable future holds another alternative of hope.
Labels:
helium-3,
space energy
Sunday, September 22, 2013
'Naming the Dead’ project will name and number people killed by drone airstrikes to challenge CIA claims of no civilian deaths
from rawstory.com: A project launched on Monday aims to record properly the names and numbers of people who are killed by US drone airstrikes in Pakistan.
The website, “Naming the Dead”, is an initiative by the Bureau of Investigative Journalism (TBIJ), a not-for-profit organisation that has won awards for its work exposing some of the realities of the covert drone wars that are being run by the US and UK militaries in Afghanistan, Pakistan, Yemen and Somalia.
It aims to keep as comprehensive a record as possible of the victims of drone airstrikes in Pakistan, after research revealed that only one in five of the victims of the 370 airstrikes that have taken place have been identified outside their own, often remote, communities.
At least 2,537 people are reported to have been killed by drone strikes in the country, with some estimates suggesting up to a quarter may have been civilians, although the TBIJ plans to name both civilians and militants using a mixture of media reports, court documents, academic studies and researchers on the ground.
The objective, said TBIJ deputy editor Rachel Oldroyd, is to take these deaths out of obscurity and make it easier to test statements about the nature and use of drones. US authorities have been reluctant to acknowledge any civilian deaths caused by the drone operations, which have been going on since 2006. The CIA has claimed a high rate of killings of militants, saying that strikes since May 2010 have killed more than 600 militants but no civilians. This claim is contested by experts, journalists and researchers on the ground.
Jennifer Gibson, a lawyer with legal campaign group Reprieve, has backed the project, saying: “All we have is the US government saying, ‘trust us, these are bad guys we are killing, trust us’. We can’t start to get to the bottom of who is being killed until we know the names of those who are being killed.”
The TBIJ is backed by the US Freedom of the Press Foundation and has been raising money for the project for the past eight months through crowdsourcing.
On Monday the first names will be published, in both English and Urdu, of which 200 are adult civilians, 95 are children and 255 are militants.
The website, “Naming the Dead”, is an initiative by the Bureau of Investigative Journalism (TBIJ), a not-for-profit organisation that has won awards for its work exposing some of the realities of the covert drone wars that are being run by the US and UK militaries in Afghanistan, Pakistan, Yemen and Somalia.
It aims to keep as comprehensive a record as possible of the victims of drone airstrikes in Pakistan, after research revealed that only one in five of the victims of the 370 airstrikes that have taken place have been identified outside their own, often remote, communities.
At least 2,537 people are reported to have been killed by drone strikes in the country, with some estimates suggesting up to a quarter may have been civilians, although the TBIJ plans to name both civilians and militants using a mixture of media reports, court documents, academic studies and researchers on the ground.
The objective, said TBIJ deputy editor Rachel Oldroyd, is to take these deaths out of obscurity and make it easier to test statements about the nature and use of drones. US authorities have been reluctant to acknowledge any civilian deaths caused by the drone operations, which have been going on since 2006. The CIA has claimed a high rate of killings of militants, saying that strikes since May 2010 have killed more than 600 militants but no civilians. This claim is contested by experts, journalists and researchers on the ground.
Jennifer Gibson, a lawyer with legal campaign group Reprieve, has backed the project, saying: “All we have is the US government saying, ‘trust us, these are bad guys we are killing, trust us’. We can’t start to get to the bottom of who is being killed until we know the names of those who are being killed.”
The TBIJ is backed by the US Freedom of the Press Foundation and has been raising money for the project for the past eight months through crowdsourcing.
On Monday the first names will be published, in both English and Urdu, of which 200 are adult civilians, 95 are children and 255 are militants.
Thursday, September 19, 2013
Apple 'Can Read Your iMessages Whenever They Want' Researchers Claim
from slate.com: Apple says that when people communicate using its iMessage service, their chats are secured using strong encryption. But security researchers are questioning the company’s claims after uncovering what they say is a flaw that enables the messages to be spied on.
Back in April, Apple’s iMessage service attracted attention after a document showed that the Drug Enforcement Agency (DEA) was complaining internally about not being able to snoop on communications sent using the service. Apple has consistently said that the messages are exchanged using "secure end-to-end encryption," meaning it can’t hand them over to authorities. Even after the technology giant was linked to the National Security Agency ‘s PRISM surveillance program in June, it put out a statement reiterating that iMessage conversations “are protected by end-to-end encryption so no one but the sender and receiver can see or read them. Apple cannot decrypt that data.”
However, it seems that the service is not as secure as Apple would like to have you believe. Two researchers at the security firm Quarkslab claim that they have been studying the protocol used by iMessage, and that “Apple can technically read your iMessages whenever they want.” The researchers, who are due to present their findings at the HITB Security Conference in Asia in October, have apparently found a way to circumvent the encryption using a so-called “man-in-the-middle” attack, which usually involves a hacker covertly bypassing the encryption by using a fake security certificate.
That this may be possible with iMessage is not evidence that Apple has been covertly reading people’s messages, but it does mean that the company’s encryption is vulnerable to being exploited by a sophisticated hacker group or spy agency. One of the Quarkslab researchers told Techcrunch that “the iMessage protocol is strong,” though added that “Apple or a powerful institution (NSA is randomly chosen as an example) could tamper with it.” The researchers say that they are planning to release a tool that will shield against potential iMessage snooping attacks, and hope to work with Apple to strengthen the security of the service. Apple had not responded to a request for comment at time of publication.
Back in April, Apple’s iMessage service attracted attention after a document showed that the Drug Enforcement Agency (DEA) was complaining internally about not being able to snoop on communications sent using the service. Apple has consistently said that the messages are exchanged using "secure end-to-end encryption," meaning it can’t hand them over to authorities. Even after the technology giant was linked to the National Security Agency ‘s PRISM surveillance program in June, it put out a statement reiterating that iMessage conversations “are protected by end-to-end encryption so no one but the sender and receiver can see or read them. Apple cannot decrypt that data.”
However, it seems that the service is not as secure as Apple would like to have you believe. Two researchers at the security firm Quarkslab claim that they have been studying the protocol used by iMessage, and that “Apple can technically read your iMessages whenever they want.” The researchers, who are due to present their findings at the HITB Security Conference in Asia in October, have apparently found a way to circumvent the encryption using a so-called “man-in-the-middle” attack, which usually involves a hacker covertly bypassing the encryption by using a fake security certificate.
That this may be possible with iMessage is not evidence that Apple has been covertly reading people’s messages, but it does mean that the company’s encryption is vulnerable to being exploited by a sophisticated hacker group or spy agency. One of the Quarkslab researchers told Techcrunch that “the iMessage protocol is strong,” though added that “Apple or a powerful institution (NSA is randomly chosen as an example) could tamper with it.” The researchers say that they are planning to release a tool that will shield against potential iMessage snooping attacks, and hope to work with Apple to strengthen the security of the service. Apple had not responded to a request for comment at time of publication.
Labels:
apple,
DEA,
encryption,
imessage,
spying
Wednesday, September 18, 2013
Brazil’s President Cancels White House Visit Over NSA Spying
'Unhappy' With Administration's Response to Surveillance
from antiwar.com: NSA surveillance is a big deal in a lot of countries, but few more than Brazil, where media outlets have covered the spying intensively, and detailed US surveillance of government leaders as well as espionage against major Brazilian companies.The diplomatic fallout for the US was already significant, but is getting worse, as Brazil has announced that they are cancelling a planned state visit by President Dilma Rousseff to the White House.
Brazilian officials say that the move was the response to their annoyance with the Obama Administration’s responses to their complaints about the NSA. The administration says the move was simply meant to “avoid controversy.”
Rousseff’s office has been intensely critical of the NSA surveillance, dubbing it a violation of national sovereignty, and had previously warned the US that the visit could be shelved if they didn’t provide suitable explanations for the NSA’s misdeeds. Needless to say, they didn’t.
11m Users Abandon #Facebook on Privacy Concerns
from alalam.ir: Millions of Facebook users are reportedly abandoning the social media giant at an unprecedented rate over privacy concerns.
New research shows Facebook has lost a total of 11 million users, nine million in the US and two million in Britain. Researchers at the University of Vienna analyzed 600 users and found they quit for reasons like privacy concerns, general dissatisfaction, shallow conversations and fear of becoming addicted.
Studies show the majority of users that quit the site were older males.
Facebook, among other tech giants, have been repeatedly under scrutiny for their lack of user privacy, including turning over thousands of user’s info to the government. In August, Infowars revealed Facebook submitted information on approximately 38,000 users in 74 countries during the first half of 2013.
Over half of the requests originated from inside of the United States. Tech giants are unable to reveal absolute numbers on how many requests they’ve submitted to because the government prohibits them from doing so.
However, companies like Google, Microsoft, Facebook and Yahoo have formed a unique alliance and are fighting back. The tech alliance is putting pressure on the Foreign Intelligence Surveillance (FISA) court by filing motions asking to publicly disclose more details about secret national intelligence requests, instead of just releasing approximations.
“We believe there is more information that the public deserves to know, and that would help foster an informed debate about whether government security programs adequately balance privacy interests when attempting to keep the public safe,” said Facebook’s general counsel Colin Stretch.
“Editor of the journal Cyberpsychology, Behaviour and Social Networking which published the findings, said: ‘Given high profile stories such as WikiLeaks and the recent NSA surveillance reports, individual citizens are becoming increasingly more wary of cyber-related privacy concerns,’”
reported Mail Online.
Facebook has also been under close examination for their recently updated “Statement of Rights and Responsibilities” policy which states users’ profile data including their profile picture, name and personal information “could show up as part of a Facebook ad their friends may see on the site,” according to a report by Mashable News Agency.
Even more controversy surrounded the social media giant when they announced the update of the “Tag Suggest” feature, which would allow facial recognition technology “to speed up the process of ‘tagging’ friends and acquaintances who appear in photos posed on the network,” reported Reuters.
As you can see, users’ concerns over privacy, or lack thereof, are certainly substantiated. However, if your information isn’t being collected through Facebook, NSA’s spy program, PRISM, is sure to scoop up your info in some other way, most likely through email or cellular data, the report said.
New research shows Facebook has lost a total of 11 million users, nine million in the US and two million in Britain. Researchers at the University of Vienna analyzed 600 users and found they quit for reasons like privacy concerns, general dissatisfaction, shallow conversations and fear of becoming addicted.
Studies show the majority of users that quit the site were older males.
Facebook, among other tech giants, have been repeatedly under scrutiny for their lack of user privacy, including turning over thousands of user’s info to the government. In August, Infowars revealed Facebook submitted information on approximately 38,000 users in 74 countries during the first half of 2013.
Over half of the requests originated from inside of the United States. Tech giants are unable to reveal absolute numbers on how many requests they’ve submitted to because the government prohibits them from doing so.
However, companies like Google, Microsoft, Facebook and Yahoo have formed a unique alliance and are fighting back. The tech alliance is putting pressure on the Foreign Intelligence Surveillance (FISA) court by filing motions asking to publicly disclose more details about secret national intelligence requests, instead of just releasing approximations.
“We believe there is more information that the public deserves to know, and that would help foster an informed debate about whether government security programs adequately balance privacy interests when attempting to keep the public safe,” said Facebook’s general counsel Colin Stretch.
“Editor of the journal Cyberpsychology, Behaviour and Social Networking which published the findings, said: ‘Given high profile stories such as WikiLeaks and the recent NSA surveillance reports, individual citizens are becoming increasingly more wary of cyber-related privacy concerns,’”
reported Mail Online.
Facebook has also been under close examination for their recently updated “Statement of Rights and Responsibilities” policy which states users’ profile data including their profile picture, name and personal information “could show up as part of a Facebook ad their friends may see on the site,” according to a report by Mashable News Agency.
Even more controversy surrounded the social media giant when they announced the update of the “Tag Suggest” feature, which would allow facial recognition technology “to speed up the process of ‘tagging’ friends and acquaintances who appear in photos posed on the network,” reported Reuters.
As you can see, users’ concerns over privacy, or lack thereof, are certainly substantiated. However, if your information isn’t being collected through Facebook, NSA’s spy program, PRISM, is sure to scoop up your info in some other way, most likely through email or cellular data, the report said.
Tuesday, September 17, 2013
Tri-City hockey crowds to be taped for U.S. security research
from tri-cityherald.com: Hockey fans at the season opener of the Tri-City Americans will have a chance to help the U.S. Department of Homeland Security improve its facial recognition capabilities.
Video will be taped by Pacific Northwest National Laboratory at the Sept. 21 game in a portion of the Toyota Center in Kennewick.
It is planned to be used by the U.S. government to test the capabilities of facial recognition software that is available or in the prototype stage.
Eventually, state-of-the-art facial recognition technologies could be used to identify terrorists and criminals in public areas, according to the national lab in Richland. The Department of Homeland Security’s Science and Technology Directorate works to make technology available to agencies ranging from local police offices to the U.S. Border Patrol, Transportation Security Administration and Immigration and Customs Enforcement.
PNNL previously has collected video at the Toyota Center for work with the Department of Homeland Security. But past video either has not captured members of the public or has been too low resolution to identify faces.
Hockey fans who don’t want to be on the video will be given options to avoid the cameras.
No video will be shot in the arena and signs will be set up in the corridors around the arena to direct people to areas without cameras. PNNL staff will be available to answer questions.
PNNL has purchased 46 seats at the arena to make sure walking areas are clear for those who don’t want their video captured, said PNNL engineer Marcia Kimura. Information explaining the project also has been mailed to season ticket holders.
“If they didn’t want to be videotaped, they could very easily not be videotaped,” said Nick Lombardo, a PNNL project manager.
Multiple cameras, bought off shelves in the Tri-Cities, will be set up in the main entrance, the hallway between sections S and W and at the concession stand at section W.
It’s not the public’s faces that PNNL is interested in capturing. Rather, they're trying to detect PNNL staffers in the crowd.
“Basically the crowd is background,” Kimura said.
Twenty PNNL staff members will be at the game to see how many times the detection software can find them and match them with already-shot still photos of them.
Half have been told to just do what they’d normally do at the game. But others have been given instructions to walk in a particular direction around the concourse at certain times or stand in line at a concession stand.
All will wear monitoring ankle bracelets that will signal when they are close enough to a monitor to potentially allow their face to be recognized.
That will help researchers know at what point on a video that detection technology could be able to find them.
PNNL will collect video to reflect different conditions that could test the capabilities of detection technology. The cameras will be placed at different heights to get high and low angles of faces and they will collect video in areas with different lighting. It also wants to get videos of crowds walking mostly in the same direction, such as at the end of the game, and crowds in which people are walking in the corridor in both directions, such as between periods.
In addition, a concession stand test is planned of people standing in straight lines and in a serpentine queue.
The video will be used to see how many of the 20 PNNL faces the technology can pick out of the crowd and also how many times the video picks out the face of a random member of the public.
That means a hockey fan’s face could be incorrectly identified as the person for whom the video is searching. However, no names of people will be collected, said Patty Wolfhope, program manager at the Department of Homeland Security. And only "government researchers" [emphasis added] not the technology developers, will see the video.
The season opener between the Americans and Spokane Chiefs could be the first of several tests, including more at Toyota Center games later in the season and possibly at another location.
PNNL may need to collect more videos showing different conditions, including some with longer lines than might be found at Toyota Center games.
The Toyota Center agreed to be the site for the video, one of several projects it has helped PNNL with in recent years.
“I think it’s in our best interest to help facilitate the development of the technology,” said Cory Pearson, executive director of VenuWorks, which operates the center. “It’s in everybody’s best interest.”
Lower-resolution video was collected at hockey games at the Toyota Center in 2008 for Department of Homeland Security work to develop screening for explosives, and improvements in explosive screening could improve security at public places, such as sports complexes. The current work could provide information that is valuable as facilities are designed to best handle crowds, Pearson said.
The video that is collected at the game and future events will provide a set database, allowing an apples-to-apples comparison of the performance of different facial recognition technologies, Lombardo said. The project may not only help the Department of Homeland Security assess the readiness of technology available, but also help it inform developers on where improvements could be made.
Video will be taped by Pacific Northwest National Laboratory at the Sept. 21 game in a portion of the Toyota Center in Kennewick.
It is planned to be used by the U.S. government to test the capabilities of facial recognition software that is available or in the prototype stage.
Eventually, state-of-the-art facial recognition technologies could be used to identify terrorists and criminals in public areas, according to the national lab in Richland. The Department of Homeland Security’s Science and Technology Directorate works to make technology available to agencies ranging from local police offices to the U.S. Border Patrol, Transportation Security Administration and Immigration and Customs Enforcement.
PNNL previously has collected video at the Toyota Center for work with the Department of Homeland Security. But past video either has not captured members of the public or has been too low resolution to identify faces.
Hockey fans who don’t want to be on the video will be given options to avoid the cameras.
No video will be shot in the arena and signs will be set up in the corridors around the arena to direct people to areas without cameras. PNNL staff will be available to answer questions.
PNNL has purchased 46 seats at the arena to make sure walking areas are clear for those who don’t want their video captured, said PNNL engineer Marcia Kimura. Information explaining the project also has been mailed to season ticket holders.
“If they didn’t want to be videotaped, they could very easily not be videotaped,” said Nick Lombardo, a PNNL project manager.
Multiple cameras, bought off shelves in the Tri-Cities, will be set up in the main entrance, the hallway between sections S and W and at the concession stand at section W.
It’s not the public’s faces that PNNL is interested in capturing. Rather, they're trying to detect PNNL staffers in the crowd.
“Basically the crowd is background,” Kimura said.
Twenty PNNL staff members will be at the game to see how many times the detection software can find them and match them with already-shot still photos of them.
Half have been told to just do what they’d normally do at the game. But others have been given instructions to walk in a particular direction around the concourse at certain times or stand in line at a concession stand.
All will wear monitoring ankle bracelets that will signal when they are close enough to a monitor to potentially allow their face to be recognized.
That will help researchers know at what point on a video that detection technology could be able to find them.
PNNL will collect video to reflect different conditions that could test the capabilities of detection technology. The cameras will be placed at different heights to get high and low angles of faces and they will collect video in areas with different lighting. It also wants to get videos of crowds walking mostly in the same direction, such as at the end of the game, and crowds in which people are walking in the corridor in both directions, such as between periods.
In addition, a concession stand test is planned of people standing in straight lines and in a serpentine queue.
The video will be used to see how many of the 20 PNNL faces the technology can pick out of the crowd and also how many times the video picks out the face of a random member of the public.
That means a hockey fan’s face could be incorrectly identified as the person for whom the video is searching. However, no names of people will be collected, said Patty Wolfhope, program manager at the Department of Homeland Security. And only "government researchers" [emphasis added] not the technology developers, will see the video.
The season opener between the Americans and Spokane Chiefs could be the first of several tests, including more at Toyota Center games later in the season and possibly at another location.
PNNL may need to collect more videos showing different conditions, including some with longer lines than might be found at Toyota Center games.
The Toyota Center agreed to be the site for the video, one of several projects it has helped PNNL with in recent years.
“I think it’s in our best interest to help facilitate the development of the technology,” said Cory Pearson, executive director of VenuWorks, which operates the center. “It’s in everybody’s best interest.”
Lower-resolution video was collected at hockey games at the Toyota Center in 2008 for Department of Homeland Security work to develop screening for explosives, and improvements in explosive screening could improve security at public places, such as sports complexes. The current work could provide information that is valuable as facilities are designed to best handle crowds, Pearson said.
The video that is collected at the game and future events will provide a set database, allowing an apples-to-apples comparison of the performance of different facial recognition technologies, Lombardo said. The project may not only help the Department of Homeland Security assess the readiness of technology available, but also help it inform developers on where improvements could be made.
U.S. Telcos Have Never Challenged #NSA Demands for Your Metadata
from wired.com: Since at least 2006 a secret spy court has continuously compelled the nation’s carriers to hand over records of every telephone call made to, from, or within the United States.
But none of the phone companies have ever challenged the orders in court, according to an August 29 opinion (.pdf) by the Foreign Intelligence Surveillance Court, which was declassified today.
“To this date, no holder of records who has received an Order to produce bulk telephony metadata has challenged the legality of such an Order,” reads the ruling. “Indeed, no recipient of any Section 215 Order has challenged the legality of such an Order, despite the explicit statutory mechanism for doing so.”
The FISC orders cited Section 215 of the Patriot Act to require phone companies like Verizon and AT&T to hand over the phone numbers of both parties involved in all calls, the international mobile subscriber identity (IMSI) number for mobile callers, calling card numbers used in the call, and the time and duration of the calls.
To be sure, any challenge to the surveillance program would have been done before the court in secret, and it’s unlikely one would have been successful.
That carriers willfully provided the metadata without blinking a legal eye, however, is cause for alarm, as the telcos appear to be the only ones so far with legal standing to make a challenge to the bulk collection orders. The Electronic Frontier Foundation, American Civil Liberties and others have brought challenges, but the legal fight on whether they have the right to sue remains undecided.
The bulk collection program came to public light in June, when the Guardian published a FISC order on the topic leaked to the media outlet by NSA whistleblower Edward Snowden.
The court declassified (.pdf) an opinion today in the wake of Snowden’s leaks.
“This Court is mindful that this matter comes before it at a time when unprecedented disclosures have been made about this and other highly-sensitive programs designed to obtain foreign intelligence information and carry out counterterrorism investigations. According to NSA Director Gen. Keith Alexander, the disclosures have caused ‘significant and irreversible damage to our nation,’” according to the opinion.
The metadata surveillance became lawful with a 2006 update to the Patriot Act. But it’s been reported that most major carriers were providing the NSA with bulk metadata voluntarily before then in the wake of the 2001 terror attacks.
So the Electronic Frontier Foundation sued the nation’s carriers. After a San Francisco federal judge refused to toss the lawsuit, Congress in 2008 passed legislation immunizing the telcos from ever being sued for forwarding customer data to the NSA.
“It’s disappointing that the telecoms did not stand up for their users,” Kurt Ospahl, an EFF staff attorney, said in a telephone interview.
The opinion declassified today spells out the court’s interpretation of why it is legal under the Patriot Act that all calling records can be forwarded to the NSA. It also notes that there is no adversarial process, meaning without a third-party challenger, the court relies solely on the government’s assertions. Every 90 days the court orders carriers to forward all calling metadata on a rolling basis.
“To ensure adherence to its Orders, this Court has the authority to oversee compliance … and requires the government to notify the Court in writing immediately concerning any instance of non-compliance. According to the government, in the prior authorization period there have been no compliance incidents,” the court wrote.
The telcos we contacted for this story did not return calls for comment or were not immediately prepared to comment.
A day after the Guardian‘s story, however, Verizon declined to acknowledge the program but also said it was just following orders.
“Verizon continually takes steps to safeguard its customers’ privacy. Nevertheless, the law authorizes the federal courts to order a company to provide information in certain circumstances, and if Verizon were to receive such an order, we would be required to comply,” Randy Milch, Verizon’s general counsel, said in a letter to employees.
On the other hand, tech companies have been pushing for transparency. They are demanding the NSA allow them to be more transparent about what type of customer data they are secretly required to share with the NSA.
But none of the phone companies have ever challenged the orders in court, according to an August 29 opinion (.pdf) by the Foreign Intelligence Surveillance Court, which was declassified today.
“To this date, no holder of records who has received an Order to produce bulk telephony metadata has challenged the legality of such an Order,” reads the ruling. “Indeed, no recipient of any Section 215 Order has challenged the legality of such an Order, despite the explicit statutory mechanism for doing so.”
The FISC orders cited Section 215 of the Patriot Act to require phone companies like Verizon and AT&T to hand over the phone numbers of both parties involved in all calls, the international mobile subscriber identity (IMSI) number for mobile callers, calling card numbers used in the call, and the time and duration of the calls.
To be sure, any challenge to the surveillance program would have been done before the court in secret, and it’s unlikely one would have been successful.
That carriers willfully provided the metadata without blinking a legal eye, however, is cause for alarm, as the telcos appear to be the only ones so far with legal standing to make a challenge to the bulk collection orders. The Electronic Frontier Foundation, American Civil Liberties and others have brought challenges, but the legal fight on whether they have the right to sue remains undecided.
The bulk collection program came to public light in June, when the Guardian published a FISC order on the topic leaked to the media outlet by NSA whistleblower Edward Snowden.
The court declassified (.pdf) an opinion today in the wake of Snowden’s leaks.
“This Court is mindful that this matter comes before it at a time when unprecedented disclosures have been made about this and other highly-sensitive programs designed to obtain foreign intelligence information and carry out counterterrorism investigations. According to NSA Director Gen. Keith Alexander, the disclosures have caused ‘significant and irreversible damage to our nation,’” according to the opinion.
The metadata surveillance became lawful with a 2006 update to the Patriot Act. But it’s been reported that most major carriers were providing the NSA with bulk metadata voluntarily before then in the wake of the 2001 terror attacks.
So the Electronic Frontier Foundation sued the nation’s carriers. After a San Francisco federal judge refused to toss the lawsuit, Congress in 2008 passed legislation immunizing the telcos from ever being sued for forwarding customer data to the NSA.
“It’s disappointing that the telecoms did not stand up for their users,” Kurt Ospahl, an EFF staff attorney, said in a telephone interview.
The opinion declassified today spells out the court’s interpretation of why it is legal under the Patriot Act that all calling records can be forwarded to the NSA. It also notes that there is no adversarial process, meaning without a third-party challenger, the court relies solely on the government’s assertions. Every 90 days the court orders carriers to forward all calling metadata on a rolling basis.
“To ensure adherence to its Orders, this Court has the authority to oversee compliance … and requires the government to notify the Court in writing immediately concerning any instance of non-compliance. According to the government, in the prior authorization period there have been no compliance incidents,” the court wrote.
The telcos we contacted for this story did not return calls for comment or were not immediately prepared to comment.
A day after the Guardian‘s story, however, Verizon declined to acknowledge the program but also said it was just following orders.
“Verizon continually takes steps to safeguard its customers’ privacy. Nevertheless, the law authorizes the federal courts to order a company to provide information in certain circumstances, and if Verizon were to receive such an order, we would be required to comply,” Randy Milch, Verizon’s general counsel, said in a letter to employees.
On the other hand, tech companies have been pushing for transparency. They are demanding the NSA allow them to be more transparent about what type of customer data they are secretly required to share with the NSA.
Northrop Grumann producing more LCS mission modules
from upi.com: Three additional mission modules for the U.S. Navy's littoral combat ships are being produced by Northrop Grumman under a $25.2 million contract.
Two of the modules are for surface warfare missions and one is for mine counter-measures. Each module package is comprised of a specific set of sub-systems such as data processing equipment, sensors, and others. Each mission package involves the integration of manned and unmanned systems.
"Northrop Grumman continues to demonstrate that, as the mission package integrator, we are delivering high-quality, fully integrated mission modules," said Doug Shaffer, director of information operations and electronic attack, Northrop Grumman Aerospace Systems. "With this procurement, we will work with our customer to capture synergies across the mission module production base, enhance production and supplier base stability, and reduce cost to the Navy."
Northrop Grumman has so far delivered two surface-warfare mission modules and one mine counter-measures mission module to the Navy for littoral combat ships. Two other mine counter-measures modules and a surface warfare module are currently in production.
Labels:
littoral combat ships,
navy,
northrop grumman
Sunday, September 15, 2013
How the cops watch your tweets in real-time
from arstechnica.com: Recent leaks about the NSA's Internet spy programs have sparked renewed interest in government surveillance, though the leaks touch largely on a single form of such surveillance—the covert one. But so-called "open source intelligence" (OSINT) is also big business— and not just at the national/international level. New tools now mine everything from "the deep Web" to Facebook posts to tweets so that cops and corporations can see what locals are saying.
Due to the sheer scale of social media posts, many tools don't even aim at providing a complete picture. Others do.
For instance, consider BlueJay, the "Law Enforcement Twitter Crime Scanner," which provides real-time, geo-fenced access to every single public tweet so that local police can keep tabs on #gunfire, #meth, and #protest (yes, those are real examples) in their communities. BlueJay is the product of BrightPlanet, whose tagline is "Deep Web Intelligence" and whose board is populated with people like Admiral John Poindexter of Total Information Awareness infamy.
BlueJay allows users to enter a set of Twitter accounts, keywords, and locations to scan for within 25-mile geofences (BlueJay users can create up to five such fences), then it returns all matching tweets in real-time. If the tweets come with GPS locations, they are plotted on a map. The product can also export databases of up to 100,000 matching tweets at a time.
A look at the BlueJay interface shows it to be a fairly basic tool, but one that gets its power from full access to the Twitter "firehose" of all tweets. Users who want to search the Twitterverse have three basic options: Twitter's search API, Twitter's streaming API, or full firehouse access to Twitter from third party providers like GNIP and DataSift. The first two are free but limited; BrightPlanet notes that even the broader streaming API returns somewhere between one and 40 percent of the relevant tweets depending on Twitter's load at the moment. The firehose requires some serious infrastructure and a paid contract with Twitter, but it provides all relevant tweets.
BlueJay partners with firehose providers and touts this fact in its marketing copy: "BlueJay captures tweets from the entire Twitter stream, unlike all other products on the market that only get a fraction of the tweets that are being posted." BlueJay is meant only for local monitoring of tweets, but this also keeps the price in reach of local police departments—$150 a month.
Of course, once you have this basic data, you may want to do more with it. Say a suspect is tweeting from a GPS-enabled phone client and appears to be dealing drugs. Forget bothering with the paperwork needed to track the phone through a cell phone provider. BrightPlanet also offers GeoTime, a separate data visualization tool that can take exported BlueJay data and mine it to show where and when the target travels, what he tweets about at various locations, and where his phone resides at night. (BrightPlanet describes this as using "pattern recognition to automatically detect and annotate time-space behaviors, such as meetings, gaps, connections, clusters, and motion.)
"The bad guys are out there, and they’re talking to each other online," BrightPlanet says in its sales pitch to law enforcement. "We’re intimately familiar with OSINT needs and deliverables, and we will deliver the Deep Web Intelligence that finds the bad guys and lets you get them behind bars."
As with most general purpose surveillance tools, though, the tech can be turned to any purpose. In a sales flyer, BrightPlanet suggests using BlueJay to "monitor large public events, social unrest, gang communications, and criminally predicated individuals" to "identify potential witness and indicators for evidence" and "track department mentions." The company has also expanded its tools to provide OSINT to the pharma and financial services industries.
Do people really tweet about things like #meth? They certainly do, though not all tweets provide any sort of actionable intelligence (and many are about Breaking Bad):
Criminals do just come right out and tweet about their crimes, but BlueJay appears to be more useful as a way to "listen in" on people who would not ordinarily be talking to police. Used well, such tools should make police departments more aware of both local problems and complaints about their own work. Used less than well, it can be a bit creepy, sort of on par with having a kid's uncle listen outside her bedroom during a slumber party. And used badly, it can make a nice tool for keeping an eye on critics/dissenters.
BlueJay is a reminder that tweets are public. It's an obvious point, but one that's easy to forget. No matter how many followers you have, your tweet stream is really being broadcast to the world. And the world is watching.
Due to the sheer scale of social media posts, many tools don't even aim at providing a complete picture. Others do.
For instance, consider BlueJay, the "Law Enforcement Twitter Crime Scanner," which provides real-time, geo-fenced access to every single public tweet so that local police can keep tabs on #gunfire, #meth, and #protest (yes, those are real examples) in their communities. BlueJay is the product of BrightPlanet, whose tagline is "Deep Web Intelligence" and whose board is populated with people like Admiral John Poindexter of Total Information Awareness infamy.
BlueJay allows users to enter a set of Twitter accounts, keywords, and locations to scan for within 25-mile geofences (BlueJay users can create up to five such fences), then it returns all matching tweets in real-time. If the tweets come with GPS locations, they are plotted on a map. The product can also export databases of up to 100,000 matching tweets at a time.
A look at the BlueJay interface shows it to be a fairly basic tool, but one that gets its power from full access to the Twitter "firehose" of all tweets. Users who want to search the Twitterverse have three basic options: Twitter's search API, Twitter's streaming API, or full firehouse access to Twitter from third party providers like GNIP and DataSift. The first two are free but limited; BrightPlanet notes that even the broader streaming API returns somewhere between one and 40 percent of the relevant tweets depending on Twitter's load at the moment. The firehose requires some serious infrastructure and a paid contract with Twitter, but it provides all relevant tweets.
BlueJay partners with firehose providers and touts this fact in its marketing copy: "BlueJay captures tweets from the entire Twitter stream, unlike all other products on the market that only get a fraction of the tweets that are being posted." BlueJay is meant only for local monitoring of tweets, but this also keeps the price in reach of local police departments—$150 a month.
Of course, once you have this basic data, you may want to do more with it. Say a suspect is tweeting from a GPS-enabled phone client and appears to be dealing drugs. Forget bothering with the paperwork needed to track the phone through a cell phone provider. BrightPlanet also offers GeoTime, a separate data visualization tool that can take exported BlueJay data and mine it to show where and when the target travels, what he tweets about at various locations, and where his phone resides at night. (BrightPlanet describes this as using "pattern recognition to automatically detect and annotate time-space behaviors, such as meetings, gaps, connections, clusters, and motion.)
"The bad guys are out there, and they’re talking to each other online," BrightPlanet says in its sales pitch to law enforcement. "We’re intimately familiar with OSINT needs and deliverables, and we will deliver the Deep Web Intelligence that finds the bad guys and lets you get them behind bars."
As with most general purpose surveillance tools, though, the tech can be turned to any purpose. In a sales flyer, BrightPlanet suggests using BlueJay to "monitor large public events, social unrest, gang communications, and criminally predicated individuals" to "identify potential witness and indicators for evidence" and "track department mentions." The company has also expanded its tools to provide OSINT to the pharma and financial services industries.
Do people really tweet about things like #meth? They certainly do, though not all tweets provide any sort of actionable intelligence (and many are about Breaking Bad):
Criminals do just come right out and tweet about their crimes, but BlueJay appears to be more useful as a way to "listen in" on people who would not ordinarily be talking to police. Used well, such tools should make police departments more aware of both local problems and complaints about their own work. Used less than well, it can be a bit creepy, sort of on par with having a kid's uncle listen outside her bedroom during a slumber party. And used badly, it can make a nice tool for keeping an eye on critics/dissenters.
BlueJay is a reminder that tweets are public. It's an obvious point, but one that's easy to forget. No matter how many followers you have, your tweet stream is really being broadcast to the world. And the world is watching.
Labels:
bluejay,
bright planet,
OSINT,
police state,
surveillance,
twitter
New #Snowden Leak Reveals Secret $52.6 Billion Budget for Intelligence Agencies
from IntelliHub.com: A new leak from Edward Snowden shows a massive budget for the military spy industrial complex that is hidden from the public.
The original leaks made my Edward Snowden were enough to totally change the whole collective dialogue about government spying, but those initial leaks were merely the tip of the iceberg. There are countless other pieces of damning evidence that are slowly being leaked out over time. Some of the most recent leaks are extremely interesting, showing a secret budget of almost $53 billion dollars that went to various intelligence agencies.[1]
Here are some of the details of intelligence spending revealed in the report:
“The United States has made a considerable investment in the Intelligence Community since the terror attacks of 9/11, a time which includes wars in Iraq and Afghanistan, the Arab Spring, the proliferation of weapons of mass destruction technology, and asymmetric threats in such areas as cyber-warfare,” Director of National Intelligence James R. Clapper Jr. wrote in response to inquiries from The Post.
“Our budgets are classified as they could provide insight for foreign intelligence services to discern our top national priorities, capabilities and sources and methods that allow us to obtain information to counter threats,” he said.[3]
Sources:
[1] Unprecedented ‘black budget’ leak reveals the scope of $52 billion US spy complex – The Verge
[2] Snowden leaks intelligence ‘black budget’ to Washington Post – Aljazeera
[3] U.S. spy network’s successes, failures and objectives detailed in ‘black budget’ summary – Washington Post
The original leaks made my Edward Snowden were enough to totally change the whole collective dialogue about government spying, but those initial leaks were merely the tip of the iceberg. There are countless other pieces of damning evidence that are slowly being leaked out over time. Some of the most recent leaks are extremely interesting, showing a secret budget of almost $53 billion dollars that went to various intelligence agencies.[1]
Here are some of the details of intelligence spending revealed in the report:
- $11.5 billion of the proposed CIA budget — which overall, was up 56 percent since 2004 — was allocated to “data collection expenses” alone.
- Of the NSA’s $10.8 billion budget, $5.2 billion were marked for “management, facilities and support.”
- Of the National Reconaissance Office’s $10.3 billion, $6 billion were allocated to data collection.
- The requested budget for the National Geospatial Intelligence Program, which supplies “imagery and map-based intelligence” was up 108 percent since 2004.
- $4.4 billion went to the General Defense Intelligence Program, which assesses foreign military activity for policymakers and U.S. military chiefs.[2]
“The United States has made a considerable investment in the Intelligence Community since the terror attacks of 9/11, a time which includes wars in Iraq and Afghanistan, the Arab Spring, the proliferation of weapons of mass destruction technology, and asymmetric threats in such areas as cyber-warfare,” Director of National Intelligence James R. Clapper Jr. wrote in response to inquiries from The Post.
“Our budgets are classified as they could provide insight for foreign intelligence services to discern our top national priorities, capabilities and sources and methods that allow us to obtain information to counter threats,” he said.[3]
Sources:
[1] Unprecedented ‘black budget’ leak reveals the scope of $52 billion US spy complex – The Verge
[2] Snowden leaks intelligence ‘black budget’ to Washington Post – Aljazeera
[3] U.S. spy network’s successes, failures and objectives detailed in ‘black budget’ summary – Washington Post
Friday, September 13, 2013
FBI Admits It Controlled Tor Servers Behind Mass Malware Attack
from wired.com: It wasn’t ever seriously in doubt, but the FBI yesterday acknowledged that it secretly took control of Freedom Hosting last July, days before the servers of the largest provider of ultra-anonymous hosting were found to be serving custom malware designed to identify visitors.
Freedom Hosting’s operator, Eric Eoin Marques, had rented the servers from an unnamed commercial hosting provider in France, and paid for them from a bank account in Las Vegas. It’s not clear how the FBI took over the servers in late July, but the bureau was temporarily thwarted when Marques somehow regained access and changed the passwords, briefly locking out the FBI until it gained back control.
The new details emerged in local press reports from a Thursday bail hearing in Dublin, Ireland, where Marques, 28, is fighting extradition to America on charges that Freedom Hosting facilitated child pornography on a massive scale. He was denied bail today for the second time since his arrest in July.
Freedom Hosting was a provider of turnkey “Tor hidden service” sites — special sites, with addresses ending in .onion, that hide their geographic location behind layers of routing, and can be reached only over the Tor anonymity network. Tor hidden services are used by sites that need to evade surveillance or protect users’ privacy to an extraordinary degree – including human rights groups and journalists. But they also appeal to serious criminal elements, child-pornography traders among them.
On August 4, all the sites hosted by Freedom Hosting — some with no connection to child porn — began serving an error message with hidden code embedded in the page. Security researchers dissected the code and found it exploited a security hole in Firefox to identify users of the Tor Browser Bundle, reporting back to a mysterious server in Northern Virginia. The FBI was the obvious suspect, but declined to comment on the incident. The FBI also didn’t respond to inquiries from WIRED today.
Donahue also said Marque had been researching the possibility of moving his hosting, and his residence, to Russia. “My suspicion is he was trying to look for a place to reside to make it the most difficult to be extradited to the U.S.,” said Donahue, according to the Irish Independent.
Freedom Hosting has long been notorious for allowing child porn to live on its servers. In 2011, the hactivist collective Anonymous singled out the service for denial-of-service attacks after allegedly finding the firm hosted 95 percent of the child porn hidden services on the Tor network. In the hearing yesterday, Donahue said the service hosted at least 100 child porn sites with thousands of users, and claimed Marques had visited some of the sites himself.
Reached by phone, Marques’ lawyer declined to comment on the case. Marques faces federal charges in Maryland, where the FBI’s child-exploitation unit is based, in a case that is still under seal.
The apparent FBI-malware attack was first noticed on August 4, when all of the hidden service sites hosted by Freedom Hosting began displaying a “Down for Maintenance” message. That included at least some lawful websites, such as the secure email provider TorMail.
Some visitors looking at the source code of the maintenance page realized that it included a hidden
iframe tag that loaded a mysterious clump of Javascript code from a Verizon Business internet address. By midday, the code was being circulated and dissected all over the net. Mozilla confirmed the code exploited a critical memory management vulnerability in Firefox that was publicly reported on June 25, and is fixed in the latest version of the browser.Though many older revisions of Firefox were vulnerable to that bug, the malware only targeted Firefox 17 ESR, the version of Firefox that forms the basis of the Tor Browser Bundle – the easiest, most user-friendly package for using the Tor anonymity network. That made it clear early on that the attack was focused specifically on de-anonymizing Tor users.
Tor Browser Bundle users who installed or manually updated after June 26 were safe from the exploit, according to the Tor Project’s security advisory on the hack.
Perhaps the strongest evidence that the attack was a law enforcement or intelligence operation was the limited functionality of the malware.
The heart of the malicious Javascript was a tiny Windows executable hidden in a variable named “Magneto.” A traditional virus would use that executable to download and install a full-featured backdoor, so the hacker could come in later and steal passwords, enlist the computer in a DDoS botnet, and generally do all the other nasty things that happen to a hacked Windows box.
But the Magneto code didn’t download anything. It looked up the victim’s MAC address — a unique hardware identifier for the computer’s network or Wi-Fi card — and the victim’s Windows hostname. Then it sent it to a server in Northern Virginia server, bypassing Tor, to expose the user’s real IP address, coding the transmission as a standard HTTP web request.
“The attackers spent a reasonable amount of time writing a reliable exploit, and a fairly customized payload, and it doesn’t allow them to download a backdoor or conduct any secondary activity,” said Vlad Tsyrklevich, who reverse-engineered the Magneto code, at the time.
The malware also sent a serial number that likely ties the target to his or her visit to the hacked Freedom Hosting-hosted website.
The official IP allocation records maintained by the American Registry for Internet Numbers show the two Magneto-related IP addresses were part of a ghost block of eight addresses that have no organization listed. Those addresses trace no further than the Verizon Business data center in Ashburn, Virginia, 20 miles northwest of the Capital Beltway.
The code’s behavior, and the command-and-control server’s Virginia placement, is also consistent with what’s known about the FBI’s “computer and internet protocol address verifier,” or CIPAV, the law enforcement spyware first reported by WIRED in 2007.
Court documents and FBI files released under the FOIA have described the CIPAV as software the FBI can deliver through a browser exploit to gather information from the target’s machine and send it to an FBI server in Virginia. The FBI has been using the CIPAV since 2002 against hackers, online sexual predators, extortionists, and others, primarily to identify suspects who are disguising their location using proxy servers or anonymity services, like Tor.
Prior to the Freedom Hosting attack, the code had been used sparingly, which kept it from leaking out and being analyzed.
No date has been set for Marques’ extradition hearings, but it’s not expected to happen until next year.
Labels:
cyber attacks,
fbi,
malware,
tor
Thursday, September 12, 2013
#Voyager 1 Spacecraft Has Left Solar System
from space.com: A spacecraft from Earth has left its cosmic backyard and taken its first steps in interstellar space.
After streaking through space for nearly 35 years, NASA's robotic Voyager 1 probe finally left the solar system in August 2012, a study published today (Sept. 12) in the journal Science reports.
"Voyager has boldly gone where no probe has gone before, marking one of the most significant technological achievements in the annals of the history of science, and as it enters interstellar space, it adds a new chapter in human scientific dreams and endeavors," NASA science chief John Grunsfeld said in a statement. "Perhaps some future deep-space explorers will catch up with Voyager, our first interstellar envoy, and reflect on how this intrepid spacecraft helped enable their future." [NASA's Voyager Probes: 5 Surprising Facts]
After streaking through space for nearly 35 years, NASA's robotic Voyager 1 probe finally left the solar system in August 2012, a study published today (Sept. 12) in the journal Science reports.
"Voyager has boldly gone where no probe has gone before, marking one of the most significant technological achievements in the annals of the history of science, and as it enters interstellar space, it adds a new chapter in human scientific dreams and endeavors," NASA science chief John Grunsfeld said in a statement. "Perhaps some future deep-space explorers will catch up with Voyager, our first interstellar envoy, and reflect on how this intrepid spacecraft helped enable their future." [NASA's Voyager Probes: 5 Surprising Facts]
Labels:
solar system,
voyager 1
Wednesday, September 11, 2013
Outer space demilitarization agreement threatened by new technologies
from rawstory.com: Security experts warn weaknesses in treaties and exploitation of GPS are compromising the prohibition against space weapons.
Developments in satellite technologies and cyber-warfare are threatening the internationally agreed demilitarization of outer space, according to legal and security experts.
Weaknesses in existing treaties and military exploitation of GPS location systems are compromising the prohibition against space weapons established during the cold war, a conference in London has been told.
“Policy, law and understanding of the threat to space is lagging behind the reality of what is out there,” warned Mark Roberts, a former Ministry of Defence official who was in charge of government space policy and the UK’s “offensive cyber portfolio”.
“If you think about something unpleasant happening in cyber [warfare], someone somewhere is probably working on it.” One state or another is likely to be devising mechanisms to disable satellities through cyber-attacks, he said.
Professor Sa’id Mosteshar, director of the London Institute of Space Policy and Law, who organised the conference, said: “We are moving rapidly into an era when most space assets have dual use: civilian and military. There have been UN resolutions on the prevention of an arms race in outer space. Every country has voted in favour with the exception of the USA and Israel.”
The disabling of satellites would have a disastrous impact on society, knocking out GPS navigation systems and time signals. Banks, telecommunications, power and many infrastructures could fail, Roberts told the conference.
Agreements such as the 1967 Outer Space treaty and the 1979 Moon treaty are supposed to control the arms race in space. Some states have signed but not ratified them, said Maria Pozza, research fellow at the Lauterpacht Centre for International Law at Cambridge University.
Existing treaties do not specify where air space ends and outer space begins – although 100km (62 miles) above the Earth is becoming the accepted limit.
The Navstar constellation of satellites was used to provide surveillance of Iraq during the Gulf war in 1991. Was that, asked Pozza, an aggressive use of space, a “force-multiplier”? Satellites may have also been used to photograph and locate al-Qaida bases, Osama bin Laden or even assess future strikes against Syria.
The Chinese tested an anti-satellite weapon in 2007 that destroyed a defunct orbiting vehicle and showered debris across near Earth orbits. Other satellites have been jammed by strong radio signals. BBC transmissions to Iran were disrupted during this year’s elections through ground signals ostensibly sent from Syria, the conference was told.
In 2011, hackers gained control of the Terra Eos and Landsat satellites, Roberts said. The orbiting stations were not damaged. “The threat can now be from a laptop in someone’s bedroom,” he added.
Professor Richard Crowther, chief engineer at the UK Space Agency, said scientists were now exploring the possibility of robotic systems that grapple with and bring down disused satellites or laser weapons to clear away debris in orbit.
Both technologies, he pointed out, had a potential dual use as military weapons. 3D printing technologies would, furthermore, allow satellite operators to develop new hardware remotely in space.
The UK is formulating its space security policy, group captain Martin Johnson, deputy head of space policy at the MoD, said. Fylingdales, the Yorkshire monitoring station, has been cooperating for 50 years with the USA to enhance “space awareness” and early warning systems. The UK, Johnson said, was now working with the EU to develop a complementary space monitoring system.
Labels:
cyberwar,
gps,
outer space,
satellite,
space war
L.A. schools to monitor students’ social media postings
 |
| Vladimir Kremlev for RT |
Glendale Unified School District, the third-largest in Los Angeles County, has paid Geo Listening Company over $40,000 to follow its students on social media networks. The stated aim is to prevent law-breaking, bullying and doing harm to themselves and others.
Under the scheme, the online activities of Glendale’s 13,000 middle-school and high-school students are closely monitored.
“All of the individual posts we monitor on social media networks are already made public by the students themselves. Therefore, no privacy is violated,” Geo Listening Company said, adding it does not “monitor email, SMS, MMS, phone calls, voicemails or unlock any privacy setting of a social network user.”
Geo Listening is aiming to become a market leader in aggregating and analyzing publicly available content for educational facilities’ security needs.
Since the company only tracks publicly available posts, students can evade monitoring by posting privately. But anonymous services such as Tor are coming under pressure in the US, raising the possibility that private web surfing could become a thing of the past.
Geo Listening bills its computing capabilities as “providing actionable daily reports to designated school administrators and staff, using a robust tier methodology” that does not interfere with existing school policies or procedures.
It claims it can track “bullying, cyber-bullying, despair, hate, harm, crime, vandalism, substance abuse, truancy” and much more, using popular services like Twitter, Facebook, Instagram, Picasa, Vine, Flickr, Ask.fm, YouTube, Google+ or anywhere else where people share information voluntarily.
Dick Sheehan, Glendale’s school supervisor, told the Glendale News-Press that the new service is helping the district to go “above and beyond” in matters of security.
School board member Christine Walters told the newspaper that educators simply have to be more “proactive to find ways to protect our students from ongoing harm,” because they are well aware of bullying taking place online.
“Similar to other safety measures we employ at our schools, we want to identify when our students are engaged in harmful behavior,” Walters said.
Glendale opted to learn more about its students after a 15-year-old boy, an alleged bullying victim, committed suicide by jumping out of a school window in plain view of dozens of his classmates, Glendale News-Press reported. The contract with Geo Listening was signed some time ago.
“Our ability to provide a social network monitoring service for each of your respective campuses separates our company from any other in the marketplace,” Geo Listening said, adding that its “unique service model for public and private schools also allows administrators to focus on students rather than technology.”
Cyber security experts warn, however, that students should be made aware of the monitoring, or they will fear trusting anyone.
“As a parent, I find it very Big Brother-ish,” said Yalda Uhls, a researcher at the Children's Digital Media Center at the University of California in Los Angeles.
Labels:
Geo Listening,
schools,
social media,
surveillance
Project aims to map giant galactic clouds of gas where stars are born
from UPI.com: Australia say they've begun to map the location of the most massive and mysterious objects in our galaxy, giant gas clouds where stars are born.
Using a giant radio telescope in southeastern Australia, the researchers have identified the galactic clouds of molecular gas -- some up to 100 light-years across -- from the carbon monoxide they contain.
"On Earth, carbon monoxide is poisonous -- a silent killer. But in space, it is the second most abundant molecule and the easiest to see," project leader Michael Burton of the University of New South Wales said.
The carbon monoxide survey of the Southern Milky Way is being carried out with a 72-foot radio telescope in Coonabarabran.
"One of the largest unresolved mysteries in galactic astronomy is how these giant, diffuse clouds form in the interstellar medium," Burton said. "This process plays a key role in the cosmic cycle of birth and death of stars."
The project is part of an international effort also searching for "dark" galactic gas clouds, unseen clouds that contain very little carbon monoxide.
Using a giant radio telescope in southeastern Australia, the researchers have identified the galactic clouds of molecular gas -- some up to 100 light-years across -- from the carbon monoxide they contain.
"On Earth, carbon monoxide is poisonous -- a silent killer. But in space, it is the second most abundant molecule and the easiest to see," project leader Michael Burton of the University of New South Wales said.
The carbon monoxide survey of the Southern Milky Way is being carried out with a 72-foot radio telescope in Coonabarabran.
"One of the largest unresolved mysteries in galactic astronomy is how these giant, diffuse clouds form in the interstellar medium," Burton said. "This process plays a key role in the cosmic cycle of birth and death of stars."
The project is part of an international effort also searching for "dark" galactic gas clouds, unseen clouds that contain very little carbon monoxide.
It is assumed these clouds are mostly made up of molecular hydrogen too cold to detect, and astronomers are using telescopes in Antarctica and Chile to search for these dark clouds based on the presence of carbon atoms rather than carbon molecules.
"Taken together, these three surveys will provide us with a picture of the distribution and movement of gas clouds in our galaxy," Burton said.
Labels:
australia,
gas clouds,
space
#NSA 'routinely' shares Americans' data with #Israel
from RT.com: The NSA regularly shares raw US intelligence data with Israel without even removing information about American citizens, according to the latest revelation published by the Guardian. The report is based on a document leaked by Edward Snowden.
On Tuesday, September 11, the Guardian published a previously undisclosed document which revealed top-secret policies in place since 2009 that are used to share personal phone and Internet data pertaining to United States citizens with American ally Israel.
The document, a five-page memorandum authorized by the National Security Agency near the beginning of US President Barack Obama’s first administration, outlines a deal between the NSA and Israel’s SIGINT National Unit, or ISNU.
“This agreement,” the memo begins, “prescribes procedures and responsibilities for ensuring” privacy safeguards are implemented to protect the Fourth Amendment rights of US citizens with regards to the direct sharing of raw intelligence collected by the NSA with its Israeli counterpart.
That data, the document later explains, includes raw traffic picked up by the American spy office such as “unevaluated and unminimized transcripts, gists, facsimiles, telex, voice and Digital Network Intelligence (DNI) metadata and content” which is never necessarily scrutinized by US officials before sent to Israeli agents.
Related:
Israel's secret intel unit spawns high-tech tycoons
But while the contents of emails and phone calls involving most US persons are fair game to be collected by Israeli intelligence, a select group of Americans are sparred from international surveillance: elected officials. The memo mandates that the Israelis must "destroy upon recognition" any communication "that is either to or from an official of the US government.” That pool of exempt persons is defined as "officials of the executive branch (including the White House, cabinet departments, and independent agencies), the US House of Representatives and Senate (member and staff) and the US federal court system (including, but not limited to, the Supreme Court)."
The Guardian notes, however, that other leaked documents uncovered as of late indicate that the US intelligence community may have reservations nonetheless with sharing info with even an ally as tried and true as Israel.
"On the one hand, the Israelis are extraordinarily good Sigint partners for us, but on the other, they target us to learn our positions on Middle East problems," a senior NSA official says in a 2008 NSA document seen by the Guardian but not published in Wednesday’s piece. "A NIE [National Intelligence Estimate] ranked them as the third most aggressive intelligence service against the US."
"One of NSA's biggest threats is actually from friendly intelligence services, like Israel. There are parameters on what NSA shares with them, but the exchange is so robust, we sometimes share more than we intended,” the Guardian quotes from the ’08 document.
According to Guardian journalists Glenn Greenwald, Laura Poitras and Ewen MacAskill, a NSA spokesperson pressed for comment wouldn’t deny the validity of the leaked document’s contents, but assured the British newspaper that "Any US person information that is acquired as a result of NSA's surveillance activities is handled under procedures that are designed to protect privacy rights.”
The latest leak comes on the 12-year anniversary of the September 11, 2001 terrorist attacks that many high-ranking US officials have used to justify the surveillance measures enacted in the decade-plus since. It also marks just more than three months since the Guardian first began published leaked NSA documents attributed to Snowden, a 30-year-old former intelligence contractor who has since relocated to Russia where he was granted asylum while avoiding espionage charges in the US.
On Tuesday, September 11, the Guardian published a previously undisclosed document which revealed top-secret policies in place since 2009 that are used to share personal phone and Internet data pertaining to United States citizens with American ally Israel.
The document, a five-page memorandum authorized by the National Security Agency near the beginning of US President Barack Obama’s first administration, outlines a deal between the NSA and Israel’s SIGINT National Unit, or ISNU.
“This agreement,” the memo begins, “prescribes procedures and responsibilities for ensuring” privacy safeguards are implemented to protect the Fourth Amendment rights of US citizens with regards to the direct sharing of raw intelligence collected by the NSA with its Israeli counterpart.
That data, the document later explains, includes raw traffic picked up by the American spy office such as “unevaluated and unminimized transcripts, gists, facsimiles, telex, voice and Digital Network Intelligence (DNI) metadata and content” which is never necessarily scrutinized by US officials before sent to Israeli agents.
Related:
Israel's secret intel unit spawns high-tech tycoons
But while the contents of emails and phone calls involving most US persons are fair game to be collected by Israeli intelligence, a select group of Americans are sparred from international surveillance: elected officials. The memo mandates that the Israelis must "destroy upon recognition" any communication "that is either to or from an official of the US government.” That pool of exempt persons is defined as "officials of the executive branch (including the White House, cabinet departments, and independent agencies), the US House of Representatives and Senate (member and staff) and the US federal court system (including, but not limited to, the Supreme Court)."
The Guardian notes, however, that other leaked documents uncovered as of late indicate that the US intelligence community may have reservations nonetheless with sharing info with even an ally as tried and true as Israel.
"On the one hand, the Israelis are extraordinarily good Sigint partners for us, but on the other, they target us to learn our positions on Middle East problems," a senior NSA official says in a 2008 NSA document seen by the Guardian but not published in Wednesday’s piece. "A NIE [National Intelligence Estimate] ranked them as the third most aggressive intelligence service against the US."
"One of NSA's biggest threats is actually from friendly intelligence services, like Israel. There are parameters on what NSA shares with them, but the exchange is so robust, we sometimes share more than we intended,” the Guardian quotes from the ’08 document.
According to Guardian journalists Glenn Greenwald, Laura Poitras and Ewen MacAskill, a NSA spokesperson pressed for comment wouldn’t deny the validity of the leaked document’s contents, but assured the British newspaper that "Any US person information that is acquired as a result of NSA's surveillance activities is handled under procedures that are designed to protect privacy rights.”
The latest leak comes on the 12-year anniversary of the September 11, 2001 terrorist attacks that many high-ranking US officials have used to justify the surveillance measures enacted in the decade-plus since. It also marks just more than three months since the Guardian first began published leaked NSA documents attributed to Snowden, a 30-year-old former intelligence contractor who has since relocated to Russia where he was granted asylum while avoiding espionage charges in the US.
Labels:
counter-intelligence,
data sharing,
israel,
metadata,
mossad,
nsa,
snowden
Tuesday, September 10, 2013
Declassified files detail blatant violations, abuse of #NSA domestic spying program
from RT.com: For years the National Security Agency has been violating restrictions and misusing the US domestic spying program that collected private data from US citizens, newly released declassified documents show.
The new information from Intelligence Community Documents Regarding Collection under Section 501 of the Foreign Intelligence Surveillance Act (FISA) shows that the government on a daily basis spied on Americans’ telephone numbers, calling patterns as well as users IP addresses during the surveillance of foreign terror suspects.
The information shows that between 2006 and 2009 the NSA violated the court restrictions by spying on telephone calls and lying to judges about how the data was deployed. The spying agency crossed referenced a selected list of some 16,000 phone numbers against databases which contained millions of records, thus violating the law, two senior intelligence officials told Bloomberg.
The metadata program which started in 2006 enabled the NSA to gather more information about a specific number that the agency claimed could be linked to terrorist activity. The agency also kept an alert list that was cross-referenced with new numbers to consider whether they should be added to a list of "reasonable articulable suspicion."
The NSA gathered the bulk phone records under Section 215 of the USA Patriot Act, which requires private companies to turn over evidence that is relevant to a terrorism investigation. However, the Foreign Intelligence Surveillance Court ruled that the NSA must have “reasonable, articulable suspicion” to run that number against a larger database. Only about 2,000 numbers on the list in 2009 met that legal condition, according to sources.
The released documents according to Director of National Intelligence James Clapper relate to “compliance incidents that were discovered by the NSA, reported to the FISC and the Congress, and resolved four years ago.”
The documents were released as part of a lawsuit filed by the Electronic Frontier Foundation and under growing pressure for the administration to shed light on its surveillance activities following Edward Snowden’s leaks.
The new information from Intelligence Community Documents Regarding Collection under Section 501 of the Foreign Intelligence Surveillance Act (FISA) shows that the government on a daily basis spied on Americans’ telephone numbers, calling patterns as well as users IP addresses during the surveillance of foreign terror suspects.
The information shows that between 2006 and 2009 the NSA violated the court restrictions by spying on telephone calls and lying to judges about how the data was deployed. The spying agency crossed referenced a selected list of some 16,000 phone numbers against databases which contained millions of records, thus violating the law, two senior intelligence officials told Bloomberg.
The metadata program which started in 2006 enabled the NSA to gather more information about a specific number that the agency claimed could be linked to terrorist activity. The agency also kept an alert list that was cross-referenced with new numbers to consider whether they should be added to a list of "reasonable articulable suspicion."
The NSA gathered the bulk phone records under Section 215 of the USA Patriot Act, which requires private companies to turn over evidence that is relevant to a terrorism investigation. However, the Foreign Intelligence Surveillance Court ruled that the NSA must have “reasonable, articulable suspicion” to run that number against a larger database. Only about 2,000 numbers on the list in 2009 met that legal condition, according to sources.
The released documents according to Director of National Intelligence James Clapper relate to “compliance incidents that were discovered by the NSA, reported to the FISC and the Congress, and resolved four years ago.”
The documents were released as part of a lawsuit filed by the Electronic Frontier Foundation and under growing pressure for the administration to shed light on its surveillance activities following Edward Snowden’s leaks.
New iPhone Has TouchID Fingerprint Authentication
from wired.com: When Apple bought AuthenTec for its biometrics technology — reported as one of its most expensive purchases — there was a lot of speculation about how the company would incorporate biometrics in its product line. Many speculate(d) that the new Apple iPhone...will come with a fingerprint authentication system, and there are several ways it could work, such as swiping your finger over a slit-sized reader to have the phone recognize you.
Labels:
apple,
biometrics,
fingerprints,
iphone
Thursday, September 5, 2013
US and UK spy agencies defeat privacy and security on the internet
from guardian.co.uk: US and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails, according to top-secret documents revealed by former contractor Edward Snowden.
The files show that the National Security Agency and its UK counterpart GCHQ have broadly compromised the guarantees that internet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments.
The agencies, the documents reveal, have adopted a battery of methods in their systematic and ongoing assault on what they see as one of the biggest threats to their ability to access huge swathes of internet traffic – "the use of ubiquitous encryption across the internet".
Those methods include covert measures to ensure NSA control over setting of international encryption standards, the use of supercomputers to break encryption with "brute force", and – the most closely guarded secret of all – collaboration with technology companies and internet service providers themselves.
Through these covert partnerships, the agencies have inserted secret vulnerabilities – known as backdoors or trapdoors – into commercial encryption software.
The files, from both the NSA and GCHQ, were obtained by the Guardian, and the details are being published today in partnership with the New York Times and ProPublica. They reveal:
• A 10-year NSA program against encryption technologies made a breakthrough in 2010 which made "vast amounts" of data collected through internet cable taps newly "exploitable".
• The NSA spends $250m a year on a program which, among other goals, works with technology companies to "covertly influence" their product designs.
• The secrecy of their capabilities against encryption is closely guarded, with analysts warned: "Do not ask about or speculate on sources or methods."
• The NSA describes strong decryption programs as the "price of admission for the US to maintain unrestricted access to and use of cyberspace".
• A GCHQ team has been working to develop ways into encrypted traffic on the "big four" service providers, named as Hotmail, Google, Yahoo and Facebook.
The agencies insist that the ability to defeat encryption is vital to their core missions of counter-terrorism and foreign intelligence gathering.
But security experts accused them of attacking the internet itself and the privacy of all users.
"Cryptography forms the basis for trust online," said Bruce Schneier, an encryption specialist and fellow at Harvard's Berkman Center for Internet and Society. "By deliberately undermining online security in a short-sighted effort to eavesdrop, the NSA is undermining the very fabric of the internet." Classified briefings between the agencies celebrate their success at "defeating network security and privacy".
"For the past decade, NSA has lead [sic] an aggressive, multi-pronged effort to break widely used internet encryption technologies," stated a 2010 GCHQ document. "Vast amounts of encrypted internet data which have up till now been discarded are now exploitable."
An internal agency memo noted that among British analysts shown a presentation on the NSA's progress: "Those not already briefed were gobsmacked!"
The breakthrough, which was not described in detail in the documents, meant the intelligence agencies were able to monitor "large amounts" of data flowing through the world's fibre-optic cables and break its encryption, despite assurances from internet company executives that this data was beyond the reach of government.
The key component of the NSA's battle against encryption, its collaboration with technology companies, is detailed in the US intelligence community's top-secret 2013 budget request under the heading "Sigint [signals intelligence] enabling".
 Funding for the program – $254.9m for this year – dwarfs that of the Prism program, which operates at a cost of $20m a year, according to previous NSA documents. Since 2011, the total spending on Sigint enabling has topped $800m. The program "actively engages US and foreign IT industries to covertly influence and/or overtly leverage their commercial products' designs", the document states. None of the companies involved in such partnerships are named; these details are guarded by still higher levels of classification.
Funding for the program – $254.9m for this year – dwarfs that of the Prism program, which operates at a cost of $20m a year, according to previous NSA documents. Since 2011, the total spending on Sigint enabling has topped $800m. The program "actively engages US and foreign IT industries to covertly influence and/or overtly leverage their commercial products' designs", the document states. None of the companies involved in such partnerships are named; these details are guarded by still higher levels of classification.
Among other things, the program is designed to "insert vulnerabilities into commercial encryption systems". These would be known to the NSA, but to no one else, including ordinary customers, who are tellingly referred to in the document as "adversaries".
"These design changes make the systems in question exploitable through Sigint collection … with foreknowledge of the modification. To the consumer and other adversaries, however, the systems' security remains intact."
The document sets out in clear terms the program's broad aims, including making commercial encryption software "more tractable" to NSA attacks by "shaping" the worldwide marketplace and continuing efforts to break into the encryption used by the next generation of 4G phones.
Among the specific accomplishments for 2013, the NSA expects the program to obtain access to "data flowing through a hub for a major communications provider" and to a "major internet peer-to-peer voice and text communications system".
Technology companies maintain that they work with the intelligence agencies only when legally compelled to do so. The Guardian has previously reported that Microsoft co-operated with the NSA to circumvent encryption on the Outlook.com email and chat services. The company insisted that it was obliged to comply with "existing or future lawful demands" when designing its products.
The documents show that the agency has already achieved another of the goals laid out in the budget request: to influence the international standards upon which encryption systems rely.
Independent security experts have long suspected that the NSA has been introducing weaknesses into security standards, a fact confirmed for the first time by another secret document. It shows the agency worked covertly to get its own version of a draft security standard issued by the US National Institute of Standards and Technology approved for worldwide use in 2006.
"Eventually, NSA became the sole editor," the document states.
The NSA's codeword for its decryption program, Bullrun, is taken from a major battle of the American civil war. Its British counterpart, Edgehill, is named after the first major engagement of the English civil war, more than 200 years earlier.
A classification guide for NSA employees and contractors on Bullrun outlines in broad terms its goals.
"Project Bullrun deals with NSA's abilities to defeat the encryption used in specific network communication technologies. Bullrun involves multiple sources, all of which are extremely sensitive." The document reveals that the agency has capabilities against widely used online protocols, such as HTTPS, voice-over-IP and Secure Sockets Layer (SSL), used to protect online shopping and banking.
The document also shows that the NSA's Commercial Solutions Center, ostensibly the body through which technology companies can have their security products assessed and presented to prospective government buyers, has another, more clandestine role.
It is used by the NSA to "to leverage sensitive, co-operative relationships with specific industry partners" to insert vulnerabilities into security products. Operatives were warned that this information must be kept top secret "at a minimum".
A more general NSA classification guide reveals more detail on the agency's deep partnerships with industry, and its ability to modify products. It cautions analysts that two facts must remain top secret: that NSA makes modifications to commercial encryption software and devices "to make them exploitable", and that NSA "obtains cryptographic details of commercial cryptographic information security systems through industry relationships".
The agencies have not yet cracked all encryption technologies, however, the documents suggest. Snowden appeared to confirm this during a live Q&A with Guardian readers in June. "Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on," he said before warning that NSA can frequently find ways around it as a result of weak security on the computers at either end of the communication.
The documents are scattered with warnings over the importance of maintaining absolute secrecy around decryption capabilities.
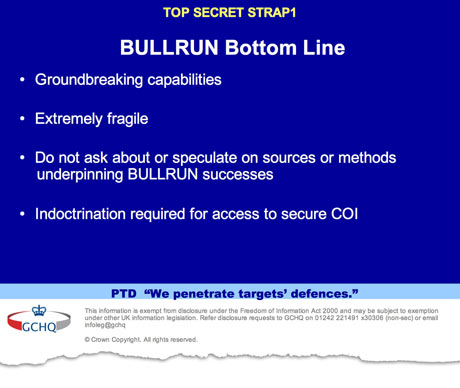 Strict guidelines were laid down at the GCHQ complex in Cheltenham, Gloucestershire, on how to discuss projects relating to decryption. Analysts were instructed: "Do not ask about or speculate on sources or methods underpinning Bullrun." This informaton was so closely guarded, according to one document, that even those with access to aspects of the program were warned: "There will be no 'need to know'."
Strict guidelines were laid down at the GCHQ complex in Cheltenham, Gloucestershire, on how to discuss projects relating to decryption. Analysts were instructed: "Do not ask about or speculate on sources or methods underpinning Bullrun." This informaton was so closely guarded, according to one document, that even those with access to aspects of the program were warned: "There will be no 'need to know'."
The agencies were supposed to be "selective in which contractors are given exposure to this information", but it was ultimately seen by Snowden, one of 850,000 people in the US with top-secret clearance. A 2009 GCHQ document spells out the significant potential consequences of any leaks, including "damage to industry relationships".
"Loss of confidence in our ability to adhere to confidentiality agreements would lead to loss of access to proprietary information that can save time when developing new capability," intelligence workers were told. Somewhat less important to GCHQ was the public's trust which was marked as a moderate risk, the document stated.
"Some exploitable products are used by the general public; some exploitable weaknesses are well known eg possibility of recovering poorly chosen passwords," it said. "Knowledge that GCHQ exploits these products and the scale of our capability would raise public awareness generating unwelcome publicity for us and our political masters."
The decryption effort is particularly important to GCHQ. Its strategic advantage from its Tempora program – direct taps on transatlantic fibre-optic cables of major telecommunications corporations – was in danger of eroding as more and more big internet companies encrypted their traffic, responding to customer demands for guaranteed privacy.
Without attention, the 2010 GCHQ document warned, the UK's "Sigint utility will degrade as information flows changes, new applications are developed (and deployed) at pace and widespread encryption becomes more commonplace." Documents show that Edgehill's initial aim was to decode the encrypted traffic certified by three major (unnamed) internet companies and 30 types of Virtual Private Network (VPN) – used by businesses to provide secure remote access to their systems. By 2015, GCHQ hoped to have cracked the codes used by 15 major internet companies, and 300 VPNs.
Another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as 'certificates', that might be vulnerable to being cracked by GCHQ supercomputers.
Analysts on the Edgehill project were working on ways into the networks of major webmail providers as part of the decryption project. A quarterly update from 2012 notes the project's team "continue to work on understanding" the big four communication providers, named in the document as Hotmail, Google, Yahoo and Facebook, adding "work has predominantly been focused this quarter on Google due to new access opportunities being developed".
To help secure an insider advantage, GCHQ also established a Humint Operations Team (HOT). Humint, short for "human intelligence" refers to information gleaned directly from sources or undercover agents.
This GCHQ team was, according to an internal document, "responsible for identifying, recruiting and running covert agents in the global telecommunications industry."
"This enables GCHQ to tackle some of its most challenging targets," the report said. The efforts made by the NSA and GCHQ against encryption technologies may have negative consequences for all internet users, experts warn.
"Backdoors are fundamentally in conflict with good security," said Christopher Soghoian, principal technologist and senior policy analyst at the American Civil Liberties Union. "Backdoors expose all users of a backdoored system, not just intelligence agency targets, to heightened risk of data compromise." This is because the insertion of backdoors in a software product, particularly those that can be used to obtain unencrypted user communications or data, significantly increases the difficulty of designing a secure product."
This was a view echoed in a recent paper by Stephanie Pell, a former prosecutor at the US Department of Justice and non-resident fellow at the Center for Internet and Security at Stanford Law School.
"[An] encrypted communications system with a lawful interception back door is far more likely to result in the catastrophic loss of communications confidentiality than a system that never has access to the unencrypted communications of its users," she states.
Intelligence officials asked the Guardian, New York Times and ProPublica not to publish this article, saying that it might prompt foreign targets to switch to new forms of encryption or communications that would be harder to collect or read.
The three organisations removed some specific facts but decided to publish the story because of the value of a public debate about government actions that weaken the most powerful tools for protecting the privacy of internet users in the US and worldwide.
The files show that the National Security Agency and its UK counterpart GCHQ have broadly compromised the guarantees that internet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments.
The agencies, the documents reveal, have adopted a battery of methods in their systematic and ongoing assault on what they see as one of the biggest threats to their ability to access huge swathes of internet traffic – "the use of ubiquitous encryption across the internet".
Those methods include covert measures to ensure NSA control over setting of international encryption standards, the use of supercomputers to break encryption with "brute force", and – the most closely guarded secret of all – collaboration with technology companies and internet service providers themselves.
Through these covert partnerships, the agencies have inserted secret vulnerabilities – known as backdoors or trapdoors – into commercial encryption software.
The files, from both the NSA and GCHQ, were obtained by the Guardian, and the details are being published today in partnership with the New York Times and ProPublica. They reveal:
• A 10-year NSA program against encryption technologies made a breakthrough in 2010 which made "vast amounts" of data collected through internet cable taps newly "exploitable".
• The NSA spends $250m a year on a program which, among other goals, works with technology companies to "covertly influence" their product designs.
• The secrecy of their capabilities against encryption is closely guarded, with analysts warned: "Do not ask about or speculate on sources or methods."
• The NSA describes strong decryption programs as the "price of admission for the US to maintain unrestricted access to and use of cyberspace".
• A GCHQ team has been working to develop ways into encrypted traffic on the "big four" service providers, named as Hotmail, Google, Yahoo and Facebook.
The agencies insist that the ability to defeat encryption is vital to their core missions of counter-terrorism and foreign intelligence gathering.
But security experts accused them of attacking the internet itself and the privacy of all users.
"Cryptography forms the basis for trust online," said Bruce Schneier, an encryption specialist and fellow at Harvard's Berkman Center for Internet and Society. "By deliberately undermining online security in a short-sighted effort to eavesdrop, the NSA is undermining the very fabric of the internet." Classified briefings between the agencies celebrate their success at "defeating network security and privacy".
"For the past decade, NSA has lead [sic] an aggressive, multi-pronged effort to break widely used internet encryption technologies," stated a 2010 GCHQ document. "Vast amounts of encrypted internet data which have up till now been discarded are now exploitable."
An internal agency memo noted that among British analysts shown a presentation on the NSA's progress: "Those not already briefed were gobsmacked!"
The breakthrough, which was not described in detail in the documents, meant the intelligence agencies were able to monitor "large amounts" of data flowing through the world's fibre-optic cables and break its encryption, despite assurances from internet company executives that this data was beyond the reach of government.
The key component of the NSA's battle against encryption, its collaboration with technology companies, is detailed in the US intelligence community's top-secret 2013 budget request under the heading "Sigint [signals intelligence] enabling".

Classified briefings between the NSA and GCHQ celebrate their success at 'defeating network security and privacy'. Photograph: Guardian
Among other things, the program is designed to "insert vulnerabilities into commercial encryption systems". These would be known to the NSA, but to no one else, including ordinary customers, who are tellingly referred to in the document as "adversaries".
"These design changes make the systems in question exploitable through Sigint collection … with foreknowledge of the modification. To the consumer and other adversaries, however, the systems' security remains intact."
The document sets out in clear terms the program's broad aims, including making commercial encryption software "more tractable" to NSA attacks by "shaping" the worldwide marketplace and continuing efforts to break into the encryption used by the next generation of 4G phones.
Among the specific accomplishments for 2013, the NSA expects the program to obtain access to "data flowing through a hub for a major communications provider" and to a "major internet peer-to-peer voice and text communications system".
Technology companies maintain that they work with the intelligence agencies only when legally compelled to do so. The Guardian has previously reported that Microsoft co-operated with the NSA to circumvent encryption on the Outlook.com email and chat services. The company insisted that it was obliged to comply with "existing or future lawful demands" when designing its products.
The documents show that the agency has already achieved another of the goals laid out in the budget request: to influence the international standards upon which encryption systems rely.
Independent security experts have long suspected that the NSA has been introducing weaknesses into security standards, a fact confirmed for the first time by another secret document. It shows the agency worked covertly to get its own version of a draft security standard issued by the US National Institute of Standards and Technology approved for worldwide use in 2006.
"Eventually, NSA became the sole editor," the document states.
The NSA's codeword for its decryption program, Bullrun, is taken from a major battle of the American civil war. Its British counterpart, Edgehill, is named after the first major engagement of the English civil war, more than 200 years earlier.
A classification guide for NSA employees and contractors on Bullrun outlines in broad terms its goals.
"Project Bullrun deals with NSA's abilities to defeat the encryption used in specific network communication technologies. Bullrun involves multiple sources, all of which are extremely sensitive." The document reveals that the agency has capabilities against widely used online protocols, such as HTTPS, voice-over-IP and Secure Sockets Layer (SSL), used to protect online shopping and banking.
The document also shows that the NSA's Commercial Solutions Center, ostensibly the body through which technology companies can have their security products assessed and presented to prospective government buyers, has another, more clandestine role.
It is used by the NSA to "to leverage sensitive, co-operative relationships with specific industry partners" to insert vulnerabilities into security products. Operatives were warned that this information must be kept top secret "at a minimum".
A more general NSA classification guide reveals more detail on the agency's deep partnerships with industry, and its ability to modify products. It cautions analysts that two facts must remain top secret: that NSA makes modifications to commercial encryption software and devices "to make them exploitable", and that NSA "obtains cryptographic details of commercial cryptographic information security systems through industry relationships".
The agencies have not yet cracked all encryption technologies, however, the documents suggest. Snowden appeared to confirm this during a live Q&A with Guardian readers in June. "Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on," he said before warning that NSA can frequently find ways around it as a result of weak security on the computers at either end of the communication.
The documents are scattered with warnings over the importance of maintaining absolute secrecy around decryption capabilities.

A slide showing that the secrecy of the agencies' capabilities against encryption is closely guarded. Photograph: Guardian
The agencies were supposed to be "selective in which contractors are given exposure to this information", but it was ultimately seen by Snowden, one of 850,000 people in the US with top-secret clearance. A 2009 GCHQ document spells out the significant potential consequences of any leaks, including "damage to industry relationships".
"Loss of confidence in our ability to adhere to confidentiality agreements would lead to loss of access to proprietary information that can save time when developing new capability," intelligence workers were told. Somewhat less important to GCHQ was the public's trust which was marked as a moderate risk, the document stated.
"Some exploitable products are used by the general public; some exploitable weaknesses are well known eg possibility of recovering poorly chosen passwords," it said. "Knowledge that GCHQ exploits these products and the scale of our capability would raise public awareness generating unwelcome publicity for us and our political masters."
The decryption effort is particularly important to GCHQ. Its strategic advantage from its Tempora program – direct taps on transatlantic fibre-optic cables of major telecommunications corporations – was in danger of eroding as more and more big internet companies encrypted their traffic, responding to customer demands for guaranteed privacy.
Without attention, the 2010 GCHQ document warned, the UK's "Sigint utility will degrade as information flows changes, new applications are developed (and deployed) at pace and widespread encryption becomes more commonplace." Documents show that Edgehill's initial aim was to decode the encrypted traffic certified by three major (unnamed) internet companies and 30 types of Virtual Private Network (VPN) – used by businesses to provide secure remote access to their systems. By 2015, GCHQ hoped to have cracked the codes used by 15 major internet companies, and 300 VPNs.
Another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as 'certificates', that might be vulnerable to being cracked by GCHQ supercomputers.
Analysts on the Edgehill project were working on ways into the networks of major webmail providers as part of the decryption project. A quarterly update from 2012 notes the project's team "continue to work on understanding" the big four communication providers, named in the document as Hotmail, Google, Yahoo and Facebook, adding "work has predominantly been focused this quarter on Google due to new access opportunities being developed".
To help secure an insider advantage, GCHQ also established a Humint Operations Team (HOT). Humint, short for "human intelligence" refers to information gleaned directly from sources or undercover agents.
This GCHQ team was, according to an internal document, "responsible for identifying, recruiting and running covert agents in the global telecommunications industry."
"This enables GCHQ to tackle some of its most challenging targets," the report said. The efforts made by the NSA and GCHQ against encryption technologies may have negative consequences for all internet users, experts warn.
"Backdoors are fundamentally in conflict with good security," said Christopher Soghoian, principal technologist and senior policy analyst at the American Civil Liberties Union. "Backdoors expose all users of a backdoored system, not just intelligence agency targets, to heightened risk of data compromise." This is because the insertion of backdoors in a software product, particularly those that can be used to obtain unencrypted user communications or data, significantly increases the difficulty of designing a secure product."
This was a view echoed in a recent paper by Stephanie Pell, a former prosecutor at the US Department of Justice and non-resident fellow at the Center for Internet and Security at Stanford Law School.
"[An] encrypted communications system with a lawful interception back door is far more likely to result in the catastrophic loss of communications confidentiality than a system that never has access to the unencrypted communications of its users," she states.
Intelligence officials asked the Guardian, New York Times and ProPublica not to publish this article, saying that it might prompt foreign targets to switch to new forms of encryption or communications that would be harder to collect or read.
The three organisations removed some specific facts but decided to publish the story because of the value of a public debate about government actions that weaken the most powerful tools for protecting the privacy of internet users in the US and worldwide.
Labels:
fibre optics,
gchq,
nsa,
prism,
sigint,
snowden,
spying,
surveillance
Subscribe to:
Posts (Atom)


















