from huffingtonpost.com: The United Kingdom's new internet filters promise to block much more than just pornography, according to a report by the digital advocacy organization Open Rights Group.
Last week, Prime Minister David Cameron announced online porn would soon become automatically blocked in order to "protect children and their innocence." The filters will be implemented by the UK's major internet service providers, which encompass 95% of British web users.
Based on conversations with several ISPs, Open Rights Group says the new "parental controls" will reach far beyond pornography. By default, the controls will block access to "violent material," "extremist and terrorist related content," "anorexia and eating disorder websites," and "suicide related websites."
In addition, the new settings will censor websites that mention alcohol or smoking. The filter will even block "web forums" and "esoteric material," though Open Rights Group does not specify what these categories would include.
The Independent notes the filters implemented by the four main private internet providers will be "default-on," meaning users must explicitly choose to turn them off. Users can decide to keep certain filters while turning others off.
Making the filters default means most people will keep them, according to Open Rights Group Executive Director Jim Killock. "We know that people stick with defaults: this is part of the idea behind 'nudge theory' and 'choice architecture' that is popular with Cameron."
According to Cameron, the new parental control settings will be turned on for all new broadband subscribers "by the end of the year."
Wednesday, July 31, 2013
Look Who’s Monitoring Social Media Now
from nextgov.com: In case there was any doubt who’s monitoring what we post to social media sites, count the Secret Service in the mix.
The agency posted a solicitation Monday seeking software to monitor social media sites for “real-time open source intelligence.”
The full description of what the Secret Service is after is only available to vendors who request it and prove their credentials.
Such tools typically mine through publicly available tweets, Facebook posts and posts to other social media sites such as Reddit and Quora looking for intelligence about people or events. They’re distinct from controversial tools used by the National Security Agency and disclosed by leaker Edward Snowden, which are seemingly capable of monitoring private posts.
A recent social media privacy guide printed by the government’s Chief Information Officers Council lists intelligence gathering as a legitimate government use of social media, provided it complies with federal laws and executive orders.
The policy also approves of so-called “situational awareness” social media monitoring by non-law enforcement or intelligence agencies, provided the agency levels with the public about the sort of information it’s looking for and how it will use it. Such monitoring programs can be used to gauge how the public is responding to a particular government initiative.
The full description of what the Secret Service is after is only available to vendors who request it and prove their credentials.
Such tools typically mine through publicly available tweets, Facebook posts and posts to other social media sites such as Reddit and Quora looking for intelligence about people or events. They’re distinct from controversial tools used by the National Security Agency and disclosed by leaker Edward Snowden, which are seemingly capable of monitoring private posts.
A recent social media privacy guide printed by the government’s Chief Information Officers Council lists intelligence gathering as a legitimate government use of social media, provided it complies with federal laws and executive orders.
The policy also approves of so-called “situational awareness” social media monitoring by non-law enforcement or intelligence agencies, provided the agency levels with the public about the sort of information it’s looking for and how it will use it. Such monitoring programs can be used to gauge how the public is responding to a particular government initiative.
Labels:
secret service,
social media,
surveillance
Tuesday, July 30, 2013
#BradleyManning verdict brings anger, disappointment – and relief
from theguardian.com: Transparency campaigners condemned the harsh sentence in prospect for Bradley Manning, but journalists and lawyers closely associated with the trial were relieved with the acquittal for the most serious charge – that he "aided the enemy" by transmitting state secrets to WikiLeaks. In a statement, Manning's family said they were disappointed by so many guilty findings – he was deemed to be guilty of 17 of the 22 counts against him in their entirety and three others in an amended form. But the statement, written by a US-based relative, said the family was "happy that Judge Lind agreed with us that Brad never intended to help America's enemies in any way."
Friday, July 26, 2013
Asian Spying Said to Focus on U.S. Radiation-Hardened Electronics
from nationaljournal.com: The Pentagon has documented a sharp increase in military espionage from the Asia-Pacific region that focuses on specialized electronics designed to withstand radiation, such as that caused by nuclear warfare or accidents, according to an official review released last week.
For a number of years, foreign entities from East Asia and the Pacific “have demonstrated a strong interest in obtaining export-controlled U.S. rad-hard circuitry,” states the report by the Pentagon’s Defense Security Service, referring to radiation-hardened electronics.
Radiation hardening is a process by which electric components are made to withstand the effects of ionizing radiation released in a nuclear explosion, by commercial atomic reactors or the sun.
These strengthened circuits “have applications in nuclear weapons, aerospace vehicles, ballistic missiles, and other electronics used in environments subject to radiation,” the review reads.
A number of Asia-Pacific nations with growing space programs could be motivated to seek out information about radiation-resistant technology.
The fiscal 2012 DSS report did not specifically single out China as the principal culprit behind this type of spying. However, it is generally understood that Beijing is the biggest perpetrator of digital espionage in the region and is also keenly interested in improving its own strategic military capabilities.
The Chinese People’s Liberation Army is believed to be concerned about the possibility of an atomic electromagnetic pulse attack -- that is, one aimed at neutralizing its nuclear deterrent or other strategic assets that rely on electronics to operate. Additionally, China could be developing EMP weapons of its own, according to a declassified 2005 U.S. Army intelligence report.
North Korea may similarly take an interest in protecting its ballistic missiles from an EMP strike; however, the isolated nation is not believed to conduct weapons espionage to the degree that China does.
In a strike optimized for electromagnetic pulse, a nuclear warhead would be detonated far above a country. The attack could send out large amounts of radiation with the intention of confusing or simply frying the electrical systems below, including those used to run weapon systems. Some U.S. lawmakers worry about the possibility of the United States coming under this form of disruptive assault.
An alternative explanation for the intense Asia-Pacific interest is that a number of nations there with developing space capabilities likely would be interested in making sure their space-based systems are built to withstand things like solar flares and cosmic rays, according to the report. Australia, China, Japan, and South Korea all have space programs of varying size and ambitions.
The Defense Security Service, which works to limit unauthorized access to U.S. weapon system details, found that rad-hard electronics “will very likely remain highly sought after” in the future.
More broadly, the Pentagon organization has seen a major uptick in espionage efforts by Asian nations aimed at gaining backdoor knowledge of U.S. missile systems.
From fiscal 2011 to fiscal 2012, defense contractors working on U.S. missile programs self-reported an 86 percent increase in instances of attempted foreign espionage. Of these attempts, more than half came from organizations connected to the Asia-Pacific region, the Defense Security Service said.
“Foreign entities, especially those linked to countries with mature missile programs, increasingly focused collection efforts on U.S. missile technology, usually aimed at particular missile subsystems,” the report found.
Among the U.S. missile systems targeted in fiscal 2012 by intelligence collectors in this region were the submarine-launched Trident ballistic missile, the tactical Tomahawk missile, the Standard Missile 3 interceptor, the Patriot Advanced Capability 3 interceptor and the Ground Based Interceptor, according to the DSS report.
In its tracking of foreign espionage efforts, the Pentagon branch cites a number of espionage efforts under the umbrella of “collection activities.” These methods include cyber spying, attempts to acquire technology, outright requests for technical information, and foreign visits.
For the first time ever in fiscal 2012, cyber sleuthing -- termed “suspicious network activity” in the report -- was the No.1 collection method used by foreign organizations. It supplanted in rank both attempted acquisition and requests for information, which were the first and second most preferred methods, respectively, in fiscal 2011.
What is particularly troubling to the U.S. military about this change is that it has become more difficult to detect spying when it occurs; cyber espionage is harder to track than the more traditional spying methods.
“These changes meant that more direct and transparent methods were increasingly displaced by more indirect and opaque methods,” the DSS office found.
Labels:
asia,
electronics,
radiation
Wednesday, July 24, 2013
#DARPA looking to build underwater drone 'mothership'
from RT.com: The US Defense Advanced Research Projects Agency (DARPA) has announced plans to develop an unmanned, submersible 'mother ship' to transport and deploy aerial and underwater drones.
The much-vaunted DARPA, which is tasked with expanding technology and science for use in defense projects, is now looking to build an unmanned undersea system that can deploy stealthy drones, both of the flying variety and unmanned underwater vehicles (UUVs), via a large carrier craft.
“The Hydra large UUV is to use modular payloads inside a standardized enclosure to deploy a mix of UAVs and UUVs, depending on the military situation. Hydra will integrate existing and emerging technologies in new ways to create an alternate means of delivering a variety of payloads close to where they’re needed.”
Based on current available technology, drones will be launched under the surface of the water much as submarines currently launch cruise missiles, within encapsulated vehicles that then surface and allow drones to launch into the air.
Though the Hydra project appears to be in its beginning stages, it would seem that much of the technology already in use by the US Navy can be adapted. Similarly, the rate at which the US has deployed increasingly sophisticated iterations of its conventional drones suggests that defense contractors could quickly adapt units to be usable with the new Hydra vessel.
Raytheon’s 6 lb. Switchblade drone, for example, which is 2 feet in length and can be carried in a backpack is already being adapted for launch from submarines. Other smaller, insect-like drones currently being developed by DARPA could all conceivably be useful for the Hydra project as well.
Currently DARPA is also looking into ways to launch and land drones from smaller surface ships, such as the Navy’s Littoral class, under a program dubbed the Tactically Exploited Reconnaissance Node (TERN).
According to DARPA, which announced the Tern program specifications only a few months ago, it is looking to give the US Navy the capabilities to launch drones without the need for large aircraft carriers or land bases.
Currently the Navy is limited to using only a handful of drone models, including the ScanEagle drone, and the Fire Scout unmanned helicopter based on Littoral Combat Ships.
In conjunction with the new Hydra project, it seems that DARPA is looking to modify the American navy into a force capable of deploying versatile unmanned robots throughout the globe.
The much-vaunted DARPA, which is tasked with expanding technology and science for use in defense projects, is now looking to build an unmanned undersea system that can deploy stealthy drones, both of the flying variety and unmanned underwater vehicles (UUVs), via a large carrier craft.
“The Hydra large UUV is to use modular payloads inside a standardized enclosure to deploy a mix of UAVs and UUVs, depending on the military situation. Hydra will integrate existing and emerging technologies in new ways to create an alternate means of delivering a variety of payloads close to where they’re needed.”
Based on current available technology, drones will be launched under the surface of the water much as submarines currently launch cruise missiles, within encapsulated vehicles that then surface and allow drones to launch into the air.
Though the Hydra project appears to be in its beginning stages, it would seem that much of the technology already in use by the US Navy can be adapted. Similarly, the rate at which the US has deployed increasingly sophisticated iterations of its conventional drones suggests that defense contractors could quickly adapt units to be usable with the new Hydra vessel.
Raytheon’s 6 lb. Switchblade drone, for example, which is 2 feet in length and can be carried in a backpack is already being adapted for launch from submarines. Other smaller, insect-like drones currently being developed by DARPA could all conceivably be useful for the Hydra project as well.
Currently DARPA is also looking into ways to launch and land drones from smaller surface ships, such as the Navy’s Littoral class, under a program dubbed the Tactically Exploited Reconnaissance Node (TERN).
According to DARPA, which announced the Tern program specifications only a few months ago, it is looking to give the US Navy the capabilities to launch drones without the need for large aircraft carriers or land bases.
Currently the Navy is limited to using only a handful of drone models, including the ScanEagle drone, and the Fire Scout unmanned helicopter based on Littoral Combat Ships.
In conjunction with the new Hydra project, it seems that DARPA is looking to modify the American navy into a force capable of deploying versatile unmanned robots throughout the globe.
The Truth About Edward Snowden
from FreedomainRadio.com: Stefan Molyneux discusses the truth about Edward Snowden and breaks down the history, origin, legality, and the terrifying reality of warrantless wiretapping, data collection and government spying.
Labels:
nsa,
snowden,
video,
wiretapping
Monday, July 22, 2013
#NSA Can Reportedly Track Phones Even When They're Turned Off
from slate.com: The NSA has a diverse range of surveillance capabilities—from monitoring Google Maps use to sifting through millions of phone call records and spying on Web searches.
But it doesn’t end there. The agency can also track down the location of a cellphone even if the handset is turned off, according to a new report.
On Monday, the Washington Post published a story focusing on how massively the NSA has grown since the 9/11 attacks. Buried within it, there was a small but striking detail: By September 2004, the NSA had developed a technique that was dubbed “The Find” by special operations officers. The technique, the Post reports, was used in Iraq and “enabled the agency to find cellphones even when they were turned off.” This helped identify “thousands of new targets, including members of a burgeoning al-Qaeda-sponsored insurgency in Iraq,” according to members of the special operations unit interviewed by the Post.
It is not explained in the report exactly how this technique worked. But to spy on phones when they are turned off, agencies would usually have to infect the handset with a Trojan that would force it to continue emitting a signal if the phone is in standby mode, unless the battery is removed. In most cases, when you turn your phone off—even if you do not remove the battery—it will stop communicating with nearby cell towers and can be traced only to the location it was in when it was powered down.
In 2006, it was reported that the FBI had deployed spyware to infect suspects’ mobile phones and record data even when they were turned off. The NSA may have resorted to a similar method in Iraq, albeit on a much larger scale by infecting thousands of users at one time. Though difficult, the mass targeting of populations with Trojan spyware is possible—and not unheard of. In 2009, for instance, thousands of BlackBerry users in the United Arab Emirates were targeted with spyware that was disguised as a legitimate update. The update drained users’ batteries and was eventually exposed by researchers, who identified that it had apparently been designed by U.S. firm SS8, which sells “lawful interception” tools to help governments conduct surveillance of communications.
In recent weeks, the NSA’s surveillance programs—both domestic and international—have been the subject of intense scrutiny following a series of leaked secret documents. The NSA says that a vast database that it maintains on phone calls made by millions of Americans does not include location data. But the revelation that the agency has developed a technique that apparently enables it to monitor thousands of cellphones—even when turned off—is likely to only inflame civil liberties groups’ concerns, prompting further questions about the full extent of the agency’s spying efforts.
But it doesn’t end there. The agency can also track down the location of a cellphone even if the handset is turned off, according to a new report.
On Monday, the Washington Post published a story focusing on how massively the NSA has grown since the 9/11 attacks. Buried within it, there was a small but striking detail: By September 2004, the NSA had developed a technique that was dubbed “The Find” by special operations officers. The technique, the Post reports, was used in Iraq and “enabled the agency to find cellphones even when they were turned off.” This helped identify “thousands of new targets, including members of a burgeoning al-Qaeda-sponsored insurgency in Iraq,” according to members of the special operations unit interviewed by the Post.
It is not explained in the report exactly how this technique worked. But to spy on phones when they are turned off, agencies would usually have to infect the handset with a Trojan that would force it to continue emitting a signal if the phone is in standby mode, unless the battery is removed. In most cases, when you turn your phone off—even if you do not remove the battery—it will stop communicating with nearby cell towers and can be traced only to the location it was in when it was powered down.
In 2006, it was reported that the FBI had deployed spyware to infect suspects’ mobile phones and record data even when they were turned off. The NSA may have resorted to a similar method in Iraq, albeit on a much larger scale by infecting thousands of users at one time. Though difficult, the mass targeting of populations with Trojan spyware is possible—and not unheard of. In 2009, for instance, thousands of BlackBerry users in the United Arab Emirates were targeted with spyware that was disguised as a legitimate update. The update drained users’ batteries and was eventually exposed by researchers, who identified that it had apparently been designed by U.S. firm SS8, which sells “lawful interception” tools to help governments conduct surveillance of communications.
In recent weeks, the NSA’s surveillance programs—both domestic and international—have been the subject of intense scrutiny following a series of leaked secret documents. The NSA says that a vast database that it maintains on phone calls made by millions of Americans does not include location data. But the revelation that the agency has developed a technique that apparently enables it to monitor thousands of cellphones—even when turned off—is likely to only inflame civil liberties groups’ concerns, prompting further questions about the full extent of the agency’s spying efforts.
Labels:
cell phone,
nsa,
tracking
UK: Online pornography to be blocked by default, PM announces
from Big Brother Co: Most households in the UK will have pornography blocked by their internet provider unless they choose to receive it, David Cameron has announced.
In addition, the prime minister said possessing online pornography depicting rape would become illegal in England and Wales - in line with Scotland.
Mr Cameron warned in a speech that access to online pornography was "corroding childhood".
The new measures will apply to both existing and new customers.
He told the BBC he expected a "row" with service providers who, he said in his speech, were "not doing enough to take responsibility" despite having a "moral duty" to do so.
He also warned he could have to "force action" by changing the law and that, if there were "technical obstacles", firms should use their "greatest brains" to overcome them.
In his speech, Mr Cameron said family-friendly filters would be automatically selected for all new customers by the end of the year - although they could choose to switch them off.
And millions of existing computer users would be contacted by their internet providers and told they must decide whether to use or not use "family-friendly filters" to restrict adult material.
The filters would apply to all devices linked to the affected home Wi-Fi network and across the public Wi-Fi network "wherever children are likely to be present".
Customers who do not click on either option - accepting or declining - will have filters activated by default, Tory MP Claire Perry, Mr Cameron's adviser on the sexualisation and commercialisation of childhood, told the BBC.
The UK's biggest internet service providers have agreed to the filters scheme meaning it should cover 95% of homes.
CONTINUE READING...
In addition, the prime minister said possessing online pornography depicting rape would become illegal in England and Wales - in line with Scotland.
Mr Cameron warned in a speech that access to online pornography was "corroding childhood".
The new measures will apply to both existing and new customers.
Mr Cameron also called for some "horrific" internet search terms to be "blacklisted", meaning they would automatically bring up no results on websites such as Google or Bing.
He also warned he could have to "force action" by changing the law and that, if there were "technical obstacles", firms should use their "greatest brains" to overcome them.
In his speech, Mr Cameron said family-friendly filters would be automatically selected for all new customers by the end of the year - although they could choose to switch them off.
And millions of existing computer users would be contacted by their internet providers and told they must decide whether to use or not use "family-friendly filters" to restrict adult material.
The filters would apply to all devices linked to the affected home Wi-Fi network and across the public Wi-Fi network "wherever children are likely to be present".
Customers who do not click on either option - accepting or declining - will have filters activated by default, Tory MP Claire Perry, Mr Cameron's adviser on the sexualisation and commercialisation of childhood, told the BBC.
The UK's biggest internet service providers have agreed to the filters scheme meaning it should cover 95% of homes.
CONTINUE READING...
Labels:
big brother,
internet filtering,
porn,
uk
Thursday, July 18, 2013
New RFID ‘Smart Guns’ May Be Used By Govt to Bypass Second Amendment
from storyleak.com: The rise of ‘smart gun’ technology, which utilizes an RFID interface to allow for both the government and the manufacturer to remotely render the gun useless at any time, is the upcoming new tactic used by anti-Constitution control freaks in the effort to take away legal firearms from the hands of law-abiding citizens.
And these smart guns are coming much sooner than you think.
TriggerSmart, the manufacturer of the Orwellian weapons that already exist in various European regions thanks to branding that smart guns are the ‘safer’ alternative to real weapons, hopes to start selling smart guns within the United States as soon as possible — and you could see them make a grand entrance by 2014. But why would anyone with a brain ever buy these smart guns, which literally trace every action you take and send the data to the government for analysis?
Well, I believe that these smart guns will not simply be pushed by slick marketing via TriggerSmart and other invested corporations, but legislation that attempts to force these smart guns on the American public. As I originally covered back in March, smart guns are one of the biggest threats we face to the Second Amendment in history.
As the creators of the Big Brother weapons have already detailed in interviews, the true power behind these RFID-controlled smart guns is the concept that they are a loophole that allows for the government to disarm the people while still ‘upholding’ the Second Amendment. Essentially, it is the wet dream of anti-Constitutional mad men.
The government has tried taking away real guns from the general public, ultimately losing the war due to the fact that the public is too informed on the true statistics regarding gun control and gun defense. They cannot launch a hostile takeover of all guns within the country right now, and traitors to the nation like Dianne Feinstein are fully aware of this fact. As much as Feinstein and others would love to have ‘Mr. and Mrs. America’ turn in all of their guns, this simply will not happen in such a manner — at least not without mass warfare and bloodshed.
So what’s the next best thing? Smart guns that become paper weights at the discretion of the government.
And this is not even getting into the entire concept of how the smart guns could easily be hacked into at any point by virtually anyone.
The subject of smart guns I’m discussing right now is a glimpse into the future. In due time, the mainstream media news channels will begin discussing how great smart guns are and how they could prevent violence, as NPR has already done on a smaller scale.
It’s essential that you share this article as well as the video on the subject so that we can detail the timeline before it even happens. If we can document the truth here, and really inform people about the true reality of smart guns, we can ultimately beat the mainstream media before they even get started.
And these smart guns are coming much sooner than you think.
TriggerSmart, the manufacturer of the Orwellian weapons that already exist in various European regions thanks to branding that smart guns are the ‘safer’ alternative to real weapons, hopes to start selling smart guns within the United States as soon as possible — and you could see them make a grand entrance by 2014. But why would anyone with a brain ever buy these smart guns, which literally trace every action you take and send the data to the government for analysis?
Well, I believe that these smart guns will not simply be pushed by slick marketing via TriggerSmart and other invested corporations, but legislation that attempts to force these smart guns on the American public. As I originally covered back in March, smart guns are one of the biggest threats we face to the Second Amendment in history.
As the creators of the Big Brother weapons have already detailed in interviews, the true power behind these RFID-controlled smart guns is the concept that they are a loophole that allows for the government to disarm the people while still ‘upholding’ the Second Amendment. Essentially, it is the wet dream of anti-Constitutional mad men.
The government has tried taking away real guns from the general public, ultimately losing the war due to the fact that the public is too informed on the true statistics regarding gun control and gun defense. They cannot launch a hostile takeover of all guns within the country right now, and traitors to the nation like Dianne Feinstein are fully aware of this fact. As much as Feinstein and others would love to have ‘Mr. and Mrs. America’ turn in all of their guns, this simply will not happen in such a manner — at least not without mass warfare and bloodshed.
So what’s the next best thing? Smart guns that become paper weights at the discretion of the government.
In the event of a ‘terrorist attack’ of any kind, the government could shut down all smart guns in the area. In the event of an elevated terror alert level, there goes the guns. How about a mass shooting in your city? Better turn off the guns. Imagine if smart guns were prevalent during the Boston lockdown that followed the Boston marathon bombings, in which military-style police raided homes at gunpoint. Those smart guns would be turned off without any question.
And this is not even getting into the entire concept of how the smart guns could easily be hacked into at any point by virtually anyone.
The subject of smart guns I’m discussing right now is a glimpse into the future. In due time, the mainstream media news channels will begin discussing how great smart guns are and how they could prevent violence, as NPR has already done on a smaller scale.
It’s essential that you share this article as well as the video on the subject so that we can detail the timeline before it even happens. If we can document the truth here, and really inform people about the true reality of smart guns, we can ultimately beat the mainstream media before they even get started.
Labels:
police state,
rfid,
smart guns
Wednesday, July 17, 2013
Police Documents on License Plate Scanners Reveal Mass Tracking
from ACLU.org: Automatic license plate readers are the most widespread location tracking technology you’ve probably never heard of. Mounted on patrol cars or stationary objects like bridges, they snap photos of every passing car, recording their plate numbers, times, and locations.
At first the captured plate data was used just to check against lists of cars law enforcement hoped to locate for various reasons (to act on arrest warrants, find stolen cars, etc.). But increasingly, all of this data is being fed into massive databases that contain the location information of many millions of innocent Americans stretching back for months or even years.
This is what we have found after analyzing more than 26,000 pages of documents from police departments in cities and towns across the country, obtained through freedom of information requests by ACLU affiliates in 38 states and Washington, D.C. As it becomes increasingly clear that ours is an era of mass surveillance facilitated by ever cheaper and more powerful computing technology (think about the NSA's call logging program), it is critical we learn how this technology is being used.
License plate readers are just one example of a disturbing phenomenon: the government is increasingly using new technology to collect information about all of us, all the time, and to store it forever – providing a complete record of our lives for it to access at will.
Click Here to view a great explainer about these technologies
As is often the case with surveillance technology, there are unobjectionable – even beneficial – uses of license plate readers. We don’t object when they’re used to identify people who are driving stolen cars or are subject to an arrest warrant. But they should not become tools for tracking where each of us has driven.
License plate readers capture vast amounts of data on innocent people
Because of the way the technology works – these devices snap photos of every passing car, not just those registered to people suspected of crimes – virtually all of the data license plate readers gather is about people who are completely innocent. Data that we obtained through our records requests illustrates this point vividly:
 Why we should worry
Why we should worry
Should the government be logging for months, years, or indefinitely the movements of the other 99 percent of people, who are innocent?
The answer to this question is no. License plate reader information can be very revealing. While one snapshot at one point might not seem sensitive, as blankets of plate readers cover our streets, and as the government stores data for longer and longer, the technology quickly morphs into a powerful tracking tool.
As computer technology and storage capacity get cheaper every year, we need to prepare for a future not just where there are a few license plate reader cameras in every town, but one in which there are multiple cameras on every block.
What can location data reveal about people? Trips to places of worship, political protests, or gun ranges can be powerful indicators of people’s beliefs. Is it really the government’s business how often you go to the drug store or liquor store, what doctors you visit, and the identities of your friends? I’m sure all of us can remember something from our past that could embarrass us. If the government comes to suspect you of something in 2020, should it have access to databases stretching back years that could dig up facts about you that previously went unnoticed?
What's happening now
Law enforcement data-retention policies today are all over the map. While some police departments store data briefly, others keep it for a long time, or indefinitely.
 The government doesn’t have a great track record of using this kind of information responsibly. As our report details, the data can be abused for official purposes, like spying on protesters merely because they are exercising their constitutionally protected right to petition the government, or unofficial ones, like tracking an ex-spouse.
The government doesn’t have a great track record of using this kind of information responsibly. As our report details, the data can be abused for official purposes, like spying on protesters merely because they are exercising their constitutionally protected right to petition the government, or unofficial ones, like tracking an ex-spouse.
Prior to the rise of powerful surveillance technology, it simply wasn’t possible to watch all of the people all of the time. But as these natural limits erode and the impossible becomes possible, we have to make conscious choices about how technology should be used.
What's the right line with license plate readers?
There is a reasonable way to regulate this technology. The primary law enforcement use of these systems is to take pictures of plates to make it possible to check them against “hot lists” of cars of interest to law enforcement. This can be done virtually instantaneously. While plates that generate a “hit” may need to be stored for investigative purposes, there is no need to store plates for months or years to achieve this purpose.
That is to say, the answer to regulating license plate readers is to have strict limits on how long plate data can be retained. While we don’t recommend a specific cutoff date, we think it should be measured in days and weeks, not months and certainly not years.
To their credit, some law enforcement agencies already comply with this principle. For example, the Minnesota State Patrol deletes all data after 48 hours.
Others keep data for longer, and the rationale given is always the same: Although you can’t tell immediately that someone is committing a crime, some of those people may well be doing something wrong, goes the argument. But in our society, the government doesn’t watch all of us all the time just in case we commit a crime.
This is not just an issue we’ll have to decide in the context of license plate readers, but the most important surveillance issue of our time. Should the NSA collect all data about everyone’s calls, just in case it’s useful to identify a terrorist? Why stop there? Why not store all of the contents of the calls we make as well? And emails? This is not just about communications or public movements. It’s also about what happens inside the home. As electric companies convert to “smart grids” that provide them data about the patterns of your electricity usage, it could well become apparent when you take a shower and whether you run your dishwasher more frequently than others in your demographic profile.
License plate readers are just one manifestation of trend. Is this a test case that we can get right?
There is a lot more in the report than I’ve covered in this blog post. Give it a read – I hope you find it thought-provoking. We’ll be posting more blog posts in coming days on different aspects of what we’ve learned about license plate readers. We also invite you to go through the documents yourself.
There is more in there than we with our small staff could fully examine, so further newsworthy discoveries may still lurk within, waiting to be discovered. And join us on twitter (hashtag #autotracking) to discuss your finds.
At first the captured plate data was used just to check against lists of cars law enforcement hoped to locate for various reasons (to act on arrest warrants, find stolen cars, etc.). But increasingly, all of this data is being fed into massive databases that contain the location information of many millions of innocent Americans stretching back for months or even years.
This is what we have found after analyzing more than 26,000 pages of documents from police departments in cities and towns across the country, obtained through freedom of information requests by ACLU affiliates in 38 states and Washington, D.C. As it becomes increasingly clear that ours is an era of mass surveillance facilitated by ever cheaper and more powerful computing technology (think about the NSA's call logging program), it is critical we learn how this technology is being used.
License plate readers are just one example of a disturbing phenomenon: the government is increasingly using new technology to collect information about all of us, all the time, and to store it forever – providing a complete record of our lives for it to access at will.
Click Here to view a great explainer about these technologies
As is often the case with surveillance technology, there are unobjectionable – even beneficial – uses of license plate readers. We don’t object when they’re used to identify people who are driving stolen cars or are subject to an arrest warrant. But they should not become tools for tracking where each of us has driven.
License plate readers capture vast amounts of data on innocent people
Because of the way the technology works – these devices snap photos of every passing car, not just those registered to people suspected of crimes – virtually all of the data license plate readers gather is about people who are completely innocent. Data that we obtained through our records requests illustrates this point vividly:

Should the government be logging for months, years, or indefinitely the movements of the other 99 percent of people, who are innocent?
The answer to this question is no. License plate reader information can be very revealing. While one snapshot at one point might not seem sensitive, as blankets of plate readers cover our streets, and as the government stores data for longer and longer, the technology quickly morphs into a powerful tracking tool.
As computer technology and storage capacity get cheaper every year, we need to prepare for a future not just where there are a few license plate reader cameras in every town, but one in which there are multiple cameras on every block.
What can location data reveal about people? Trips to places of worship, political protests, or gun ranges can be powerful indicators of people’s beliefs. Is it really the government’s business how often you go to the drug store or liquor store, what doctors you visit, and the identities of your friends? I’m sure all of us can remember something from our past that could embarrass us. If the government comes to suspect you of something in 2020, should it have access to databases stretching back years that could dig up facts about you that previously went unnoticed?
What's happening now
Law enforcement data-retention policies today are all over the map. While some police departments store data briefly, others keep it for a long time, or indefinitely.

Prior to the rise of powerful surveillance technology, it simply wasn’t possible to watch all of the people all of the time. But as these natural limits erode and the impossible becomes possible, we have to make conscious choices about how technology should be used.
What's the right line with license plate readers?
There is a reasonable way to regulate this technology. The primary law enforcement use of these systems is to take pictures of plates to make it possible to check them against “hot lists” of cars of interest to law enforcement. This can be done virtually instantaneously. While plates that generate a “hit” may need to be stored for investigative purposes, there is no need to store plates for months or years to achieve this purpose.
That is to say, the answer to regulating license plate readers is to have strict limits on how long plate data can be retained. While we don’t recommend a specific cutoff date, we think it should be measured in days and weeks, not months and certainly not years.
To their credit, some law enforcement agencies already comply with this principle. For example, the Minnesota State Patrol deletes all data after 48 hours.
Others keep data for longer, and the rationale given is always the same: Although you can’t tell immediately that someone is committing a crime, some of those people may well be doing something wrong, goes the argument. But in our society, the government doesn’t watch all of us all the time just in case we commit a crime.
This is not just an issue we’ll have to decide in the context of license plate readers, but the most important surveillance issue of our time. Should the NSA collect all data about everyone’s calls, just in case it’s useful to identify a terrorist? Why stop there? Why not store all of the contents of the calls we make as well? And emails? This is not just about communications or public movements. It’s also about what happens inside the home. As electric companies convert to “smart grids” that provide them data about the patterns of your electricity usage, it could well become apparent when you take a shower and whether you run your dishwasher more frequently than others in your demographic profile.
License plate readers are just one manifestation of trend. Is this a test case that we can get right?
There is a lot more in the report than I’ve covered in this blog post. Give it a read – I hope you find it thought-provoking. We’ll be posting more blog posts in coming days on different aspects of what we’ve learned about license plate readers. We also invite you to go through the documents yourself.
There is more in there than we with our small staff could fully examine, so further newsworthy discoveries may still lurk within, waiting to be discovered. And join us on twitter (hashtag #autotracking) to discuss your finds.
Labels:
police state,
surveillance,
tracking
‘Neural dust’ brain implants could revolutionize brain-machine interfaces and allow large-scale data recording
from StratRisks.com: In a potential neuroscience breakthrough, University of California Berkeley scientists have proposed a system that allows for thousands of ultra-tiny “neural dust” chips to be inserted into the brain to monitor neural signals at high resolution and communicate data highly efficiently via ultrasound.
The neural dust design promises to overcome a serious limitation of current invasive brain-machine interfaces (BMI): the lack of an implantable neural interface system that remains viable for a lifetime. Current BMI systems are also limited to several hundred implantable recording sites, they generate tissue responses around the implanted electrodes that degrade recording performance over time, and are limited to months to a few years.
Neural dust could also provide the large-scale recording of neurons required for the Brain Research through Advancing Innovative Neurotechnologies (BRAIN) initiative, the scientists suggest.
System Concept:
Neural dust system diagram showing the placement of ultrasonic transceiver under the skull, the neural dust sensing nodes dispersed throughout the brain, and external transceiver (credit: Dongjin Seo et al.) The neural dust system has three basic elements:
The design also uses more efficient “backscatting”: instead of transmitting energy, the chips passively modulate ultrasonic energy from the sub-dural transceiver and reflect it back.
The researchers calculate that the neural dust chips can be as much as 10 million times more efficient that chips using electromagnetics (magnetic or electric signals), which have high attenuation in brain tissue. They would be encapsulated in an inert polymer or insulator film.
The arXiv paper mentions a number of challenges that need to be addressed in developing a practical system.
The neural dust design promises to overcome a serious limitation of current invasive brain-machine interfaces (BMI): the lack of an implantable neural interface system that remains viable for a lifetime. Current BMI systems are also limited to several hundred implantable recording sites, they generate tissue responses around the implanted electrodes that degrade recording performance over time, and are limited to months to a few years.
Neural dust could also provide the large-scale recording of neurons required for the Brain Research through Advancing Innovative Neurotechnologies (BRAIN) initiative, the scientists suggest.
System Concept:
Neural dust system diagram showing the placement of ultrasonic transceiver under the skull, the neural dust sensing nodes dispersed throughout the brain, and external transceiver (credit: Dongjin Seo et al.) The neural dust system has three basic elements:
- Thousands of low-power CMOS chips — neural dust — are embedded (via fine-wire arrays that are then removed) into the cortex between neurons. They detect extracellular electrophysiological signals via an electrode and a piezoelectric sensor converts ithe signals into ultrasonic signals.
- A subdural (the dura surrounds the brain and keeps in the cerebrospinal fluid) ultrasonic transceiver (transmitter+receiver) receives ultrasonic signals from the neural dust.It also powers the neural dust with ultrasonic energy.
- A battery-powered external transceiver communicates via ultrasound with the subdural transceiver and transmits the data to an external computer.
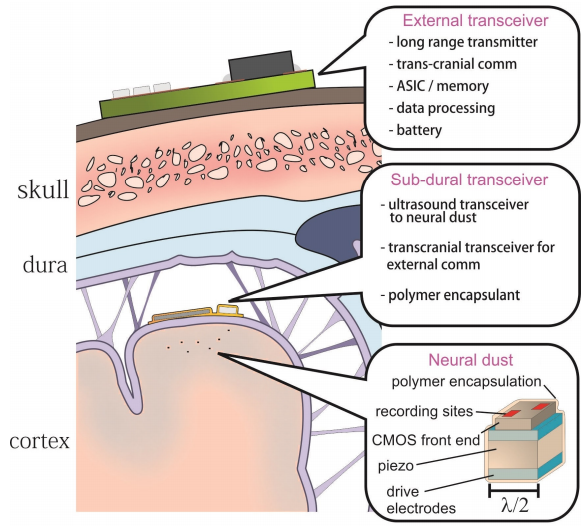
The design also uses more efficient “backscatting”: instead of transmitting energy, the chips passively modulate ultrasonic energy from the sub-dural transceiver and reflect it back.
The researchers calculate that the neural dust chips can be as much as 10 million times more efficient that chips using electromagnetics (magnetic or electric signals), which have high attenuation in brain tissue. They would be encapsulated in an inert polymer or insulator film.
The arXiv paper mentions a number of challenges that need to be addressed in developing a practical system.
Labels:
biotech,
BMI,
ray kurzweil,
transhumanism
Tuesday, July 16, 2013
Kim Dotcom Planning To Invest In Privacy Startups
from techdirt.com: We were just discussing how there's a sudden renewed interest among many entrepreneurs to build much more security and privacy conscious apps. In that post, we noted that Kim Dotcom's Mega is working on encrypted chat and email, but it appears he wants to go much further. He's now announced that he's starting a venture capital fund for privacy-focused startups as well.
Of course, it will be interesting to see what the actual details are and what comes out of it, but it's yet another sign that the revelations that have come out about widespread government surveillance many lead to a much needed refocusing on how to build much more secure and private systems in this digital era. It seems odd to think that, indirectly, the US government's highly questionable legal assault on Dotcom may eventually lead to the funding of a variety of applications and services that block out the US government's prying eyes.
Of course, it will be interesting to see what the actual details are and what comes out of it, but it's yet another sign that the revelations that have come out about widespread government surveillance many lead to a much needed refocusing on how to build much more secure and private systems in this digital era. It seems odd to think that, indirectly, the US government's highly questionable legal assault on Dotcom may eventually lead to the funding of a variety of applications and services that block out the US government's prying eyes.
Labels:
kim dotcom,
megaupload
Monday, July 15, 2013
Mining in Space – The Next Frontier?
from TheDiplomat.com: Off-Earth mining is no longer science fiction. Pacific Rim countries lead the way.
Given the rising global demand for rare-earth elements (REE) and the necessity to synthesize exotic materials for numerous high-tech applications, extra-terrestrial mining is likely to become the next race in space.
REE are used in state-of-the-art electronics, nuclear technologies, lasers, super-magnets and green-energy technology. China, the world’s largest producer of REE, restricted its abundant supplies globally in 2009, citing the need to protect the environment. In fact, it was the mismanagement of reserves and increasing domestic high-tech production that compelled Beijing to cut REE exports from its Bayan Obo mining district.
In response to Beijing’s move, REE consumers and electronic manufacturers like Japan, the U.S and South Korea accelerated terrestrial exploration of reserves to maintain their industrial supplies.
In 2011, Japan succeeded in discovering REE in ocean-bed deposits in its Pacific Exclusive Economic Zone. Apart from exploration, the Japanese trading firm Sumitomo Corporation created a joint venture – Summit Atom Rare Earth Company – with Kazakhstan’s state-run nuclear agency KazAtomProm, to extract REEs from the abundant uranium tailings in Kazakhstan. In 2012, the U.S-based Molycorp Inc. resumed operations in the long-closed Mountain Pass Rare Earth Mine in California to meet domestic demand in the civilian and defence sectors. South Korea has entered into an agreement on REE prospecting with Kyrgyzstan – probably one of the largest such projects in this unexploited mineral-rich nation.
Countries like India, Canada, Tanzania, Australia, Brazil and Vietnam have started prospecting and mining REE within their own jurisdictions; Australia has the largest mine outside China, at Mount Weld.
CONTINUE READING...
Given the rising global demand for rare-earth elements (REE) and the necessity to synthesize exotic materials for numerous high-tech applications, extra-terrestrial mining is likely to become the next race in space.
REE are used in state-of-the-art electronics, nuclear technologies, lasers, super-magnets and green-energy technology. China, the world’s largest producer of REE, restricted its abundant supplies globally in 2009, citing the need to protect the environment. In fact, it was the mismanagement of reserves and increasing domestic high-tech production that compelled Beijing to cut REE exports from its Bayan Obo mining district.
In response to Beijing’s move, REE consumers and electronic manufacturers like Japan, the U.S and South Korea accelerated terrestrial exploration of reserves to maintain their industrial supplies.
In 2011, Japan succeeded in discovering REE in ocean-bed deposits in its Pacific Exclusive Economic Zone. Apart from exploration, the Japanese trading firm Sumitomo Corporation created a joint venture – Summit Atom Rare Earth Company – with Kazakhstan’s state-run nuclear agency KazAtomProm, to extract REEs from the abundant uranium tailings in Kazakhstan. In 2012, the U.S-based Molycorp Inc. resumed operations in the long-closed Mountain Pass Rare Earth Mine in California to meet domestic demand in the civilian and defence sectors. South Korea has entered into an agreement on REE prospecting with Kyrgyzstan – probably one of the largest such projects in this unexploited mineral-rich nation.
Countries like India, Canada, Tanzania, Australia, Brazil and Vietnam have started prospecting and mining REE within their own jurisdictions; Australia has the largest mine outside China, at Mount Weld.
CONTINUE READING...
Saturday, July 13, 2013
War of the Worlds 75th Anniversary Contest Winners!
War of the Worlds 75th Anniversary Contest winners have been announced. The winner "Dead London" chosen on strength of on-location recordings. The present writer recommends other entries - great entertainment for free! You can access a prior post on War of the Worlds here for more info on original and prior anniversary recordings! Great Stuff!
Labels:
audio,
mp3,
war of the worlds
Thursday, July 11, 2013
Obama gives himself control of all communication systems in America
 from RT.com: US President Barack Obama quietly signed his name to an Executive Order on Friday, allowing the White House to control all private communications in the country in the name of national security.
from RT.com: US President Barack Obama quietly signed his name to an Executive Order on Friday, allowing the White House to control all private communications in the country in the name of national security.President Obama released his latest Executive Order on Friday, July 6, a 2,205-word statement offered as the “Assignment of National Security and Emergency Preparedness Communications Functions.” And although the president chose not to commemorate the signing with much fanfare, the powers he provides to himself and the federal government under the latest order are among the most far-reaching yet of any of his executive decisions.
“The Federal Government must have the ability to communicate at all times and under all circumstances to carry out its most critical and time sensitive missions,” the president begins the order.
“Survivable, resilient, enduring and effective communications, both domestic and international, are essential to enable the executive branch to communicate within itself and with: the legislative and judicial branches; State, local, territorial and tribal governments; private sector entities; and the public, allies and other nations.”
President Obama adds that it is necessary for the government to be able to reach anyone in the country during situations it considers "critical", writing, “Such communications must be possible under all circumstances to ensure national security, effectively manage emergencies and improve national resilience.” Later the president explains that such could be done by establishing a “joint industry-Government center that is capable of assisting in the initiation, coordination, restoration and reconstitution of NS/EP [national security and emergency preparedness] communications services or facilities under all conditions of emerging threats, crisis or emergency.”
“The views of all levels of government, the private and nonprofit sectors, and the public must inform the development of NS/EP communications policies, programs and capabilities,” he adds.
On the government’s official website for the National Communications Systems, the government explains that that “infrastructure includes wireline, wireless, satellite, cable, and broadcasting, and provides the transport networks that support the Internet and other key information systems,” suggesting that the president has indeed effectively just allowed himself to control the country’s Internet access.
In order to allow the White House to reach anyone within the US, the president has put forth a plan to establish a high-level committee calling from agents with the Department of Homeland Security, Pentagon, Federal Communications Commission and other government divisions to ensure that his new executive order can be implemented.
In explaining the order, the Electronic Privacy Information Center (EPIC) writes that the president has authorized the DHS "the authority to seize private facilities when necessary, effectively shutting down or limiting civilian communications."
In Section 5 of his order, President Obama outlines the specific department and agency responsibilities that will see through his demands. In a few paragraphs, President Obama explains that Executive Committee that will oversee his order must be supplied with “the technical support necessary to develop and maintain plans adequate to provide for the security and protection of NS/EP communications,” and that that same body will be in tasked with dispatching that communiqué “to the Federal Government and State, local, territorial and trial governments,” by means of “commercial, Government and privately owned communications resources.”
Later, the president announces that the Department of Homeland Security will be tasked with drafting a plan during the next 60 days to explain how the DHS will command the government’s Emergency Telecommunications Service, as well as other telecom conduits. In order to be able to spread the White House’s message across the country, President Obama also asks for the purchasing of equipment and services that will enable such.
Labels:
communications,
executive order,
kill switch,
obama
Revealed: How #Microsoft handed the #NSA access to encrypted messages
from guardian.co.uk: Microsoft has collaborated closely with US intelligence services to allow users' communications to be intercepted, including helping the National Security Agency to circumvent the company's own encryption, according to top-secret documents obtained by the Guardian.
The files provided by Edward Snowden illustrate the scale of co-operation between Silicon Valley and the intelligence agencies over the last three years. They also shed new light on the workings of the top-secret Prism program, which was disclosed by the Guardian and the Washington Post last month.
The documents show that:
• Microsoft helped the NSA to circumvent its encryption to address concerns that the agency would be unable to intercept web chats on the new Outlook.com portal;
• The agency already had pre-encryption stage access to email on Outlook.com, including Hotmail;
• The company worked with the FBI this year to allow the NSA easier access via Prism to its cloud storage service SkyDrive, which now has more than 250 million users worldwide;
• Microsoft also worked with the FBI's Data Intercept Unit to "understand" potential issues with a feature in Outlook.com that allows users to create email aliases;
• In July last year, nine months after Microsoft bought Skype, the NSA boasted that a new capability had tripled the amount of Skype video calls being collected through Prism;
• Material collected through Prism is routinely shared with the FBI and CIA, with one NSA document describing the program as a "team sport".
The latest NSA revelations further expose the tensions between Silicon Valley and the Obama administration. All the major tech firms are lobbying the government to allow them to disclose more fully the extent and nature of their co-operation with the NSA to meet their customers' privacy concerns. Privately, tech executives are at pains to distance themselves from claims of collaboration and teamwork given by the NSA documents, and insist the process is driven by legal compulsion.
In a statement, Microsoft said: "When we upgrade or update products we aren't absolved from the need to comply with existing or future lawful demands." The company reiterated its argument that it provides customer data "only in response to government demands and we only ever comply with orders for requests about specific accounts or identifiers".
In June, the Guardian revealed that the NSA claimed to have "direct access" through the Prism program to the systems of many major internet companies, including Microsoft, Skype, Apple, Google, Facebook and Yahoo.
Blanket orders from the secret surveillance court allow these communications to be collected without an individual warrant if the NSA operative has a 51% belief that the target is not a US citizen and is not on US soil at the time. Targeting US citizens does require an individual warrant, but the NSA is able to collect Americans' communications without a warrant if the target is a foreign national located overseas.
Since Prism's existence became public, Microsoft and the other companies listed on the NSA documents as providers have denied all knowledge of the program and insisted that the intelligence agencies do not have back doors into their systems.
Microsoft's latest marketing campaign, launched in April, emphasizes its commitment to privacy with the slogan: "Your privacy is our priority."
Similarly, Skype's privacy policy states: "Skype is committed to respecting your privacy and the confidentiality of your personal data, traffic data and communications content."
But internal NSA newsletters, marked top secret, suggest the co-operation between the intelligence community and the companies is deep and ongoing.
The latest documents come from the NSA's Special Source Operations (SSO) division, described by Snowden as the "crown jewel" of the agency. It is responsible for all programs aimed at US communications systems through corporate partnerships such as Prism.
The files show that the NSA became concerned about the interception of encrypted chats on Microsoft's Outlook.com portal from the moment the company began testing the service in July last year.
Within five months, the documents explain, Microsoft and the FBI had come up with a solution that allowed the NSA to circumvent encryption on Outlook.com chats.
A newsletter entry dated 26 December 2012 states: "MS [Microsoft], working with the FBI, developed a surveillance capability to deal" with the issue. "These solutions were successfully tested and went live 12 Dec 2012."
Two months later, in February this year, Microsoft officially launched the Outlook.com portal.
Another newsletter entry stated that NSA already had pre-encryption access to Outlook email. "For Prism collection against Hotmail, Live, and Outlook.com emails will be unaffected because Prism collects this data prior to encryption."
Microsoft's co-operation was not limited to Outlook.com. An entry dated 8 April 2013 describes how the company worked "for many months" with the FBI – which acts as the liaison between the intelligence agencies and Silicon Valley on Prism – to allow Prism access without separate authorization to its cloud storage service SkyDrive.
The document describes how this access "means that analysts will no longer have to make a special request to SSO for this – a process step that many analysts may not have known about".
The NSA explained that "this new capability will result in a much more complete and timely collection response". It continued: "This success is the result of the FBI working for many months with Microsoft to get this tasking and collection solution established."
A separate entry identified another area for collaboration. "The FBI Data Intercept Technology Unit (DITU) team is working with Microsoft to understand an additional feature in Outlook.com which allows users to create email aliases, which may affect our tasking processes."
The NSA has devoted substantial efforts in the last two years to work with Microsoft to ensure increased access to Skype, which has an estimated 663 million global users.
One document boasts that Prism monitoring of Skype video production has roughly tripled since a new capability was added on 14 July 2012. "The audio portions of these sessions have been processed correctly all along, but without the accompanying video. Now, analysts will have the complete 'picture'," it says.
Eight months before being bought by Microsoft, Skype joined the Prism program in February 2011.
According to the NSA documents, work had begun on smoothly integrating Skype into Prism in November 2010, but it was not until 4 February 2011 that the company was served with a directive to comply signed by the attorney general.
The NSA was able to start tasking Skype communications the following day, and collection began on 6 February. "Feedback indicated that a collected Skype call was very clear and the metadata looked complete," the document stated, praising the co-operation between NSA teams and the FBI.
"Collaborative teamwork was the key to the successful addition of another provider to the Prism system."
ACLU technology expert Chris Soghoian said the revelations would surprise many Skype users. "In the past, Skype made affirmative promises to users about their inability to perform wiretaps," he said.
"It's hard to square Microsoft's secret collaboration with the NSA with its high-profile efforts to compete on privacy with Google."
The information the NSA collects from Prism is routinely shared with both the FBI and CIA. A 3 August 2012 newsletter describes how the NSA has recently expanded sharing with the other two agencies.
The NSA, the entry reveals, has even automated the sharing of aspects of Prism, using software that "enables our partners to see which selectors [search terms] the National Security Agency has tasked to Prism".
The document continues: "The FBI and CIA then can request a copy of Prism collection of any selector…" As a result, the author notes: "these two activities underscore the point that Prism is a team sport!"
In its statement to the Guardian, Microsoft said:
The files provided by Edward Snowden illustrate the scale of co-operation between Silicon Valley and the intelligence agencies over the last three years. They also shed new light on the workings of the top-secret Prism program, which was disclosed by the Guardian and the Washington Post last month.
The documents show that:
• Microsoft helped the NSA to circumvent its encryption to address concerns that the agency would be unable to intercept web chats on the new Outlook.com portal;
• The agency already had pre-encryption stage access to email on Outlook.com, including Hotmail;
• The company worked with the FBI this year to allow the NSA easier access via Prism to its cloud storage service SkyDrive, which now has more than 250 million users worldwide;
• Microsoft also worked with the FBI's Data Intercept Unit to "understand" potential issues with a feature in Outlook.com that allows users to create email aliases;
• In July last year, nine months after Microsoft bought Skype, the NSA boasted that a new capability had tripled the amount of Skype video calls being collected through Prism;
• Material collected through Prism is routinely shared with the FBI and CIA, with one NSA document describing the program as a "team sport".
The latest NSA revelations further expose the tensions between Silicon Valley and the Obama administration. All the major tech firms are lobbying the government to allow them to disclose more fully the extent and nature of their co-operation with the NSA to meet their customers' privacy concerns. Privately, tech executives are at pains to distance themselves from claims of collaboration and teamwork given by the NSA documents, and insist the process is driven by legal compulsion.
In a statement, Microsoft said: "When we upgrade or update products we aren't absolved from the need to comply with existing or future lawful demands." The company reiterated its argument that it provides customer data "only in response to government demands and we only ever comply with orders for requests about specific accounts or identifiers".
In June, the Guardian revealed that the NSA claimed to have "direct access" through the Prism program to the systems of many major internet companies, including Microsoft, Skype, Apple, Google, Facebook and Yahoo.
Blanket orders from the secret surveillance court allow these communications to be collected without an individual warrant if the NSA operative has a 51% belief that the target is not a US citizen and is not on US soil at the time. Targeting US citizens does require an individual warrant, but the NSA is able to collect Americans' communications without a warrant if the target is a foreign national located overseas.
Since Prism's existence became public, Microsoft and the other companies listed on the NSA documents as providers have denied all knowledge of the program and insisted that the intelligence agencies do not have back doors into their systems.
Microsoft's latest marketing campaign, launched in April, emphasizes its commitment to privacy with the slogan: "Your privacy is our priority."
Similarly, Skype's privacy policy states: "Skype is committed to respecting your privacy and the confidentiality of your personal data, traffic data and communications content."
But internal NSA newsletters, marked top secret, suggest the co-operation between the intelligence community and the companies is deep and ongoing.
The latest documents come from the NSA's Special Source Operations (SSO) division, described by Snowden as the "crown jewel" of the agency. It is responsible for all programs aimed at US communications systems through corporate partnerships such as Prism.
The files show that the NSA became concerned about the interception of encrypted chats on Microsoft's Outlook.com portal from the moment the company began testing the service in July last year.
Within five months, the documents explain, Microsoft and the FBI had come up with a solution that allowed the NSA to circumvent encryption on Outlook.com chats.
A newsletter entry dated 26 December 2012 states: "MS [Microsoft], working with the FBI, developed a surveillance capability to deal" with the issue. "These solutions were successfully tested and went live 12 Dec 2012."
Two months later, in February this year, Microsoft officially launched the Outlook.com portal.
Another newsletter entry stated that NSA already had pre-encryption access to Outlook email. "For Prism collection against Hotmail, Live, and Outlook.com emails will be unaffected because Prism collects this data prior to encryption."
Microsoft's co-operation was not limited to Outlook.com. An entry dated 8 April 2013 describes how the company worked "for many months" with the FBI – which acts as the liaison between the intelligence agencies and Silicon Valley on Prism – to allow Prism access without separate authorization to its cloud storage service SkyDrive.
The document describes how this access "means that analysts will no longer have to make a special request to SSO for this – a process step that many analysts may not have known about".
The NSA explained that "this new capability will result in a much more complete and timely collection response". It continued: "This success is the result of the FBI working for many months with Microsoft to get this tasking and collection solution established."
A separate entry identified another area for collaboration. "The FBI Data Intercept Technology Unit (DITU) team is working with Microsoft to understand an additional feature in Outlook.com which allows users to create email aliases, which may affect our tasking processes."
The NSA has devoted substantial efforts in the last two years to work with Microsoft to ensure increased access to Skype, which has an estimated 663 million global users.
One document boasts that Prism monitoring of Skype video production has roughly tripled since a new capability was added on 14 July 2012. "The audio portions of these sessions have been processed correctly all along, but without the accompanying video. Now, analysts will have the complete 'picture'," it says.
Eight months before being bought by Microsoft, Skype joined the Prism program in February 2011.
According to the NSA documents, work had begun on smoothly integrating Skype into Prism in November 2010, but it was not until 4 February 2011 that the company was served with a directive to comply signed by the attorney general.
The NSA was able to start tasking Skype communications the following day, and collection began on 6 February. "Feedback indicated that a collected Skype call was very clear and the metadata looked complete," the document stated, praising the co-operation between NSA teams and the FBI.
"Collaborative teamwork was the key to the successful addition of another provider to the Prism system."
ACLU technology expert Chris Soghoian said the revelations would surprise many Skype users. "In the past, Skype made affirmative promises to users about their inability to perform wiretaps," he said.
"It's hard to square Microsoft's secret collaboration with the NSA with its high-profile efforts to compete on privacy with Google."
The information the NSA collects from Prism is routinely shared with both the FBI and CIA. A 3 August 2012 newsletter describes how the NSA has recently expanded sharing with the other two agencies.
The NSA, the entry reveals, has even automated the sharing of aspects of Prism, using software that "enables our partners to see which selectors [search terms] the National Security Agency has tasked to Prism".
The document continues: "The FBI and CIA then can request a copy of Prism collection of any selector…" As a result, the author notes: "these two activities underscore the point that Prism is a team sport!"
In its statement to the Guardian, Microsoft said:
We have clear principles which guide the response across our entire company to government demands for customer information for both law enforcement and national security issues. First, we take our commitments to our customers and to compliance with applicable law very seriously, so we provide customer data only in response to legal processes.
Second, our compliance team examines all demands very closely, and we reject them if we believe they aren't valid. Third, we only ever comply with orders about specific accounts or identifiers, and we would not respond to the kind of blanket orders discussed in the press over the past few weeks, as the volumes documented in our most recent disclosure clearly illustrate.
Finally when we upgrade or update products legal obligations may in some circumstances require that we maintain the ability to provide information in response to a law enforcement or national security request. There are aspects of this debate that we wish we were able to discuss more freely. That's why we've argued for additional transparency that would help everyone understand and debate these important issues.In a joint statement, Shawn Turner, spokesman for the director of National Intelligence, and Judith Emmel, spokeswoman for the NSA, said:
The articles describe court-ordered surveillance – and a US company's efforts to comply with these legally mandated requirements. The US operates its programs under a strict oversight regime, with careful monitoring by the courts, Congress and the Director of National Intelligence. Not all countries have equivalent oversight requirements to protect civil liberties and privacy.They added: "In practice, US companies put energy, focus and commitment into consistently protecting the privacy of their customers around the world, while meeting their obligations under the laws of the US and other countries in which they operate."
Dave Wigington: Geoengineering & Chemtrails
Dave Wigington makes compelling case reckless release of chemicals in our atmosphere, are destroying Earth. Wigington informs protracted droughts a direct result of chemtrails. From Geoengineering Watch website, "Global geo- engineering programs are literally ripping the atmosphere/climate, and Earths life support systems apart. The lethally toxic fallout from these same programs is poisoning every breath we take, and the entire web of life. If you think this sounds absurd, or impossible, take the time to examine the points made in this presentation, then investigate for yourself."
An impressive. highly important presentation. you should come away after viewing chilled to the bone!
An impressive. highly important presentation. you should come away after viewing chilled to the bone!
Labels:
chemtrails,
dave wigington,
geoengineering,
video
Wednesday, July 10, 2013
#NSA spied on Latin America for energy and military intel
from RT.com: The NSA’s spy program encompasses most countries in Latin America, new cables released by Edward Snowden have confirmed. The data gathered on military affairs and “commercial secrets” has provoked a flurry of furious rhetoric from regional leaders.
Brazilian daily, O Globo, which obtained the cables released by former CIA employee Edward Snowden, published a report on Tuesday detailed the National Security Agency’s initiatives in Latin America.
The US government retrieved key data on a number of issues including the oil market, drugs trade and political movements. Colombia is a top priority for the US, registering the most spy activity, with Mexico, Venezuela and Brazil following closely behind. In addition, Argentina, Ecuador, Panama, Costa Rica, Nicaragua, Honduras, Paraguay, Chile, Peru and El Salvador are under surveillance, though to a lesser degree.
According to the documents obtained by O Globo, the NSA carried out espionage in Latin America in the first quarter of 2013 using at least two data-snooping programs: ‘PRISM,’ from February 2-8 and ‘Boundless Informant’ from January through to March.
‘PRISM’ recorded metadata through Facebook, Google, Microsoft and YouTube, while ‘Boundless Informant’ monitored telephone calls and access to the internet.
O Globo also reported that the NSA gathered information through private Brazilian telecommunications companies using a program called ‘Silverzephyr.’ The daily was unable to identify the companies, but stated that using the program the US gained access to phone calls, faxes and emails.
Furthermore, the leaked information revealed the existence of data-crunching centers in Bogota, Caracas, Mexico City and Panama City and Brasilia that dealt with information intercepted from satellites.
Brazil is currently investigating telecommunication companies believed to be involved in the massive US surveillance program. The country’s president, Dilma Rousseff, was quick to react to the news, stating that if the reports of spying were confirmed it would definitely be a “violation of our sovereignty, without a doubt, just like it’s a violation of human rights.”
Brazil’s Senate foreign relations committee has requested that US ambassador Thomas Shannon to testify on the allegations. It is unclear whether Shannon, who is not legally obliged to provide testimony, will agree.
Gilberto Carvalho, a top aide to President Rousseff, called for a "very hard" response to the United States .
"If we lower our heads, they will trample all over us tomorrow," he said.
President of Argentina Cristina Fernandez de Kirchner said she hopes the US’ actions will be condemned at the next Mercosur (an economic union between Argentina, Brazil, Paraguay, Uruguay, and Venezuela) summit.
“I feel a shiver going down my spine when I see that they are spying on all of us through their services in Brazil,” she said in reference to the O Globo article.
Peruvian President Ollanta Humala, known for his pro-US stance, stated that the reports were “concerning.”
"We are against these kinds of espionage activities," he said in a televised interview. "It would be good for [Peru's] Congress to look with concern at privacy issues related to personal information."
In turn, Colombia has called on the US for an explanation for an “unauthorized” data collection program.
"In rejecting the acts of espionage that violate people's rights and intimacy as well as the international conventions on telecommunication, Colombia requests the corresponding explanations from the United States government through its ambassador to Colombia," the Colombian Foreign Ministry said in the statement.
Mexico, one of the most surveilled countries, has thus far refrained from commenting on the reports .
US whistleblower Edward Snowden, who currently has an extradition order against his name from Washington, is holed up in Moscow’s Sheremetyevo Airport unable to leave because his passport has been revoked. He has applied for political asylum in a number of Latin American countries.
Venezuela and Nicaragua have said they are currently assessing his request.
Brazilian daily, O Globo, which obtained the cables released by former CIA employee Edward Snowden, published a report on Tuesday detailed the National Security Agency’s initiatives in Latin America.
The US government retrieved key data on a number of issues including the oil market, drugs trade and political movements. Colombia is a top priority for the US, registering the most spy activity, with Mexico, Venezuela and Brazil following closely behind. In addition, Argentina, Ecuador, Panama, Costa Rica, Nicaragua, Honduras, Paraguay, Chile, Peru and El Salvador are under surveillance, though to a lesser degree.
According to the documents obtained by O Globo, the NSA carried out espionage in Latin America in the first quarter of 2013 using at least two data-snooping programs: ‘PRISM,’ from February 2-8 and ‘Boundless Informant’ from January through to March.
‘PRISM’ recorded metadata through Facebook, Google, Microsoft and YouTube, while ‘Boundless Informant’ monitored telephone calls and access to the internet.
O Globo also reported that the NSA gathered information through private Brazilian telecommunications companies using a program called ‘Silverzephyr.’ The daily was unable to identify the companies, but stated that using the program the US gained access to phone calls, faxes and emails.
Furthermore, the leaked information revealed the existence of data-crunching centers in Bogota, Caracas, Mexico City and Panama City and Brasilia that dealt with information intercepted from satellites.
Brazil is currently investigating telecommunication companies believed to be involved in the massive US surveillance program. The country’s president, Dilma Rousseff, was quick to react to the news, stating that if the reports of spying were confirmed it would definitely be a “violation of our sovereignty, without a doubt, just like it’s a violation of human rights.”
Brazil’s Senate foreign relations committee has requested that US ambassador Thomas Shannon to testify on the allegations. It is unclear whether Shannon, who is not legally obliged to provide testimony, will agree.
Gilberto Carvalho, a top aide to President Rousseff, called for a "very hard" response to the United States .
"If we lower our heads, they will trample all over us tomorrow," he said.
President of Argentina Cristina Fernandez de Kirchner said she hopes the US’ actions will be condemned at the next Mercosur (an economic union between Argentina, Brazil, Paraguay, Uruguay, and Venezuela) summit.
“I feel a shiver going down my spine when I see that they are spying on all of us through their services in Brazil,” she said in reference to the O Globo article.
Peruvian President Ollanta Humala, known for his pro-US stance, stated that the reports were “concerning.”
"We are against these kinds of espionage activities," he said in a televised interview. "It would be good for [Peru's] Congress to look with concern at privacy issues related to personal information."
In turn, Colombia has called on the US for an explanation for an “unauthorized” data collection program.
"In rejecting the acts of espionage that violate people's rights and intimacy as well as the international conventions on telecommunication, Colombia requests the corresponding explanations from the United States government through its ambassador to Colombia," the Colombian Foreign Ministry said in the statement.
Mexico, one of the most surveilled countries, has thus far refrained from commenting on the reports .
US whistleblower Edward Snowden, who currently has an extradition order against his name from Washington, is holed up in Moscow’s Sheremetyevo Airport unable to leave because his passport has been revoked. He has applied for political asylum in a number of Latin American countries.
Venezuela and Nicaragua have said they are currently assessing his request.
Labels:
boundless informant,
latin america,
nsa,
prism,
silverzephyr,
snowden,
surveillance
Tuesday, July 9, 2013
New evidence proves existence of space wind
from trueactivist.com: Scientists have revealed new evidence of space wind, confirming a theory proposed 20 years ago. ‘Plasmaspheric wind’ is an elusive phenomenon and its existence helps scientists understand how the atmosphere protects us from violent solar winds.
Proof of space wind was uncovered in a study in European Geosciences Union journal Annales Geophysicae. The so-called ‘plasmaspheric wind’ is actually created by the Earth. Essentially, an imbalance between centrifugal and pressure forces and gravitational pull causes the steady flow of ionized particles from inside the atmosphere to the magnetosphere.
The magnetosphere is the region of space surrounding the earth that is governed by the planet’s magnetic field.
“After long scrutiny of the data, there it was, a slow but steady wind, releasing about 1 kg of plasma every second into the outer magnetosphere: this corresponds to almost 90 tons every day,” said Dr Iannis Dandouras, author of the study. He added the discovery was “one of the nicest surprises I’ve ever had.”
From the data, Dandourus calculated that the winds carry plasma (superheated gas) a day from the lower atmosphere into the magnetosphere at speeds of some 5,000 kilometers per hour.
Dandourus collated data from the EU Space Agency’s Cluster mission which was launched back in 2000. The Cluster mission is made up of four satellites that monitor the relationship between the Earth’s magnetosphere and solar winds.
The study will help scientists increase their understanding of how different layers of the Earth’s atmosphere interact with each other and protect the planet from solar winds. Furthermore, the findings indicate that other planets and celestial bodies that have similar atmospheres and rotations should also generate ‘plasmasphereic wind.’
The violent solar winds composed of charged particles that are ejected from the Sun would be quite deadly to Earth’s inhabitants if it were not for the Earth’s atmosphere and magnetic field. The two work in tandem to block x-rays, ultraviolet radiation and charged particles from reaching the planet’s surface.
“[The discovery] shows how interconnected different layers of the atmosphere are in protecting Earth from solar wind,” says Dr David Neudegg from the Bureau of Meteorology’s Ionospheric Prediction Service, which monitors space weather.
Researchers first proposed the idea of the existence of space wind flowing from the lower atmosphere into the magnetosphere 20 years ago, but were unable to prove their theories.
Proof of space wind was uncovered in a study in European Geosciences Union journal Annales Geophysicae. The so-called ‘plasmaspheric wind’ is actually created by the Earth. Essentially, an imbalance between centrifugal and pressure forces and gravitational pull causes the steady flow of ionized particles from inside the atmosphere to the magnetosphere.
The magnetosphere is the region of space surrounding the earth that is governed by the planet’s magnetic field.
“After long scrutiny of the data, there it was, a slow but steady wind, releasing about 1 kg of plasma every second into the outer magnetosphere: this corresponds to almost 90 tons every day,” said Dr Iannis Dandouras, author of the study. He added the discovery was “one of the nicest surprises I’ve ever had.”
From the data, Dandourus calculated that the winds carry plasma (superheated gas) a day from the lower atmosphere into the magnetosphere at speeds of some 5,000 kilometers per hour.
Dandourus collated data from the EU Space Agency’s Cluster mission which was launched back in 2000. The Cluster mission is made up of four satellites that monitor the relationship between the Earth’s magnetosphere and solar winds.
The study will help scientists increase their understanding of how different layers of the Earth’s atmosphere interact with each other and protect the planet from solar winds. Furthermore, the findings indicate that other planets and celestial bodies that have similar atmospheres and rotations should also generate ‘plasmasphereic wind.’
The violent solar winds composed of charged particles that are ejected from the Sun would be quite deadly to Earth’s inhabitants if it were not for the Earth’s atmosphere and magnetic field. The two work in tandem to block x-rays, ultraviolet radiation and charged particles from reaching the planet’s surface.
“[The discovery] shows how interconnected different layers of the atmosphere are in protecting Earth from solar wind,” says Dr David Neudegg from the Bureau of Meteorology’s Ionospheric Prediction Service, which monitors space weather.
Researchers first proposed the idea of the existence of space wind flowing from the lower atmosphere into the magnetosphere 20 years ago, but were unable to prove their theories.
Labels:
discovery,
space wind
Monday, July 8, 2013
Snowden reveals Australia's links to US spy web
from theage.com.au: Edward Snowden has provided his first disclosure of Australian involvement in US global surveillance, identifying four facilities in the country that contribute to a key American intelligence collection program.
Classified US National Security Agency maps leaked by Mr Snowden and published by US journalist Glenn Greenwald in the Brazilian O Globo newspaper reveal the locations of dozens of US and allied signals intelligence collection sites that contribute to interception of telecommunications and internet traffic worldwide.
The US Australian Joint Defence Facility at Pine Gap near Alice Springs and three Australian Signals Directorate facilities: the Shoal Bay Receiving Station near Darwin, the Australian Defence Satellite Communications Facility at Geraldton and the naval communications station HMAS Harman outside Canberra are among contributors to the NSA's collection program codenamed X-Keyscore.
Classified US National Security Agency maps leaked by Mr Snowden and published by US journalist Glenn Greenwald in the Brazilian O Globo newspaper reveal the locations of dozens of US and allied signals intelligence collection sites that contribute to interception of telecommunications and internet traffic worldwide.
The US Australian Joint Defence Facility at Pine Gap near Alice Springs and three Australian Signals Directorate facilities: the Shoal Bay Receiving Station near Darwin, the Australian Defence Satellite Communications Facility at Geraldton and the naval communications station HMAS Harman outside Canberra are among contributors to the NSA's collection program codenamed X-Keyscore.
The New Zealand Government Security Communications Bureau facility at Waihopai near Blenheim also contributes to the program.
X-Keyscore reportedly processes all signals before they are shunted off to various "production lines" that deal with specific issues and the exploitation of different data types for analysis - variously code-named Nucleon (voice), Pinwale (video), Mainway (call records) and Marina (internet records). US intelligence expert William Arkin describes X-Keyscore as a “national Intelligence collection mission system”.
The documents published by O Globo show that US and allied signals intelligence collection facilities are distributed worldwide, located at US and allied military and other facilities as well as US embassies and consulates.
Fairfax Media recently reported the construction of a new state-of-the-art data storage facility at HMAS Harman to support the Australian signals directorate and other Australian intelligence agencies.
In an interview published in the German Der Spiegel magazine on Sunday, Mr Snowden said the NSA operates broad secret intelligence partnerships with other western governments, some of which are now complaining about its programs.
Mr Snowden said that the other partners in the "Five Eyes" intelligence alliance of the US, United Kingdom, Canada, Australia and New Zealand “sometimes go even further than the [National Security Agency] people themselves.”
He highlighted the British Government Communications Headquarters “Tempora” program as an example:
“Tempora is the first 'I save everything' approach ('full take') in the intelligence world. It sucks in all data, no matter what it is, and which rights are violated by it. ... Right now, the system is capable of saving three days' worth of traffic, but that will be optimised. Three days may perhaps not sound like a lot, but it's not just about connection metadata. 'Full take' means that the system saves everything. If you send a data packet and if makes its way through the UK, we will get it. If you download anything, and the server is in the UK, then we get it.”
Mr Snowden also argued that the “Five eyes” partnerships are organised so that authorities in each country can "insulate their political leaders from the backlash" when it became public "how grievously they're violating global privacy"
The Der Spiegel interview was conducted by US cryptography expert Jacob Appelbaum and documentary filmmaker Laura Poitras via encrypted emails shortly before Mr Snowden revealed himself publicly as the source of leaks of highly classified information on US signals intelligence and surveillance programs.
Another US NSA whistle-blower William Binney also recently disclosed that Australia was involved in the trial of an earlier US-designed Internet traffic interception and analysis program codenamed "ThinThread".
Other countries involved in the trials were the UK, Australia and Germany a decade ago. ThinThread was not adopted but Australia has also been directly involved with later collection programs codenamed "Trailblazer", "Turbulence" and "Trafficthief".
The US government has charged Mr Snowden with offences including espionage and revoked his passport.
He has been stranded at a Moscow airport for two weeks after leaving Hong Kong where the US Government has sought his extradition.
Three Latin American countries, Venezuela, Bolivia and Nicaragua, have now offered Mr Snowden political asylum after European Governments last week denied their airspace to a plane carrying the Bolivian president Evo Morales home from a conference in Moscow after the US State Department alleged that the former US intelligence contractor was on board.
Russian officials have publicly urged Mr Snowden to take up Venezuela's asylum offer. Venezuelan Foreign Minister Elias Jaua said on Sunday that his government had not yet been in contact with Mr Snowden.
Mr Jaua said he expected to consult on Monday with Russian officials. Mr Snowden is being assisted by the anti-secrecy organisation, WikiLeaks.
The documents published by O Globo show that US and allied signals intelligence collection facilities are distributed worldwide, located at US and allied military and other facilities as well as US embassies and consulates.
Fairfax Media recently reported the construction of a new state-of-the-art data storage facility at HMAS Harman to support the Australian signals directorate and other Australian intelligence agencies.
In an interview published in the German Der Spiegel magazine on Sunday, Mr Snowden said the NSA operates broad secret intelligence partnerships with other western governments, some of which are now complaining about its programs.
Mr Snowden said that the other partners in the "Five Eyes" intelligence alliance of the US, United Kingdom, Canada, Australia and New Zealand “sometimes go even further than the [National Security Agency] people themselves.”
He highlighted the British Government Communications Headquarters “Tempora” program as an example:
“Tempora is the first 'I save everything' approach ('full take') in the intelligence world. It sucks in all data, no matter what it is, and which rights are violated by it. ... Right now, the system is capable of saving three days' worth of traffic, but that will be optimised. Three days may perhaps not sound like a lot, but it's not just about connection metadata. 'Full take' means that the system saves everything. If you send a data packet and if makes its way through the UK, we will get it. If you download anything, and the server is in the UK, then we get it.”
Mr Snowden also argued that the “Five eyes” partnerships are organised so that authorities in each country can "insulate their political leaders from the backlash" when it became public "how grievously they're violating global privacy"
The Der Spiegel interview was conducted by US cryptography expert Jacob Appelbaum and documentary filmmaker Laura Poitras via encrypted emails shortly before Mr Snowden revealed himself publicly as the source of leaks of highly classified information on US signals intelligence and surveillance programs.
Another US NSA whistle-blower William Binney also recently disclosed that Australia was involved in the trial of an earlier US-designed Internet traffic interception and analysis program codenamed "ThinThread".
Other countries involved in the trials were the UK, Australia and Germany a decade ago. ThinThread was not adopted but Australia has also been directly involved with later collection programs codenamed "Trailblazer", "Turbulence" and "Trafficthief".
The US government has charged Mr Snowden with offences including espionage and revoked his passport.
He has been stranded at a Moscow airport for two weeks after leaving Hong Kong where the US Government has sought his extradition.
Three Latin American countries, Venezuela, Bolivia and Nicaragua, have now offered Mr Snowden political asylum after European Governments last week denied their airspace to a plane carrying the Bolivian president Evo Morales home from a conference in Moscow after the US State Department alleged that the former US intelligence contractor was on board.
Russian officials have publicly urged Mr Snowden to take up Venezuela's asylum offer. Venezuelan Foreign Minister Elias Jaua said on Sunday that his government had not yet been in contact with Mr Snowden.
Mr Jaua said he expected to consult on Monday with Russian officials. Mr Snowden is being assisted by the anti-secrecy organisation, WikiLeaks.
Sunday, July 7, 2013
In Secret, Court Vastly Broadens Powers of #NSA
from NYtimes.com: In more than a dozen classified rulings, the nation’s surveillance court has created a secret body of law giving the National Security Agency the power to amass vast collections of data on Americans while pursuing not only terrorism suspects, but also people possibly involved in nuclear proliferation, espionage and cyberattacks, officials say.
The special needs doctrine was originally established in 1989 by the Supreme Court in a ruling allowing the drug testing of railway workers, finding that a minimal intrusion on privacy was justified by the government’s need to combat an overriding public danger. Applying that concept more broadly, the FISA judges have ruled that the N.S.A.’s collection and examination of Americans’ communications data to track possible terrorists does not run afoul of the Fourth Amendment, the officials said.
The rulings, some nearly 100 pages long, reveal that the court has taken on a much more expansive role by regularly assessing broad constitutional questions and establishing important judicial precedents, with almost no public scrutiny, according to current and former officials familiar with the court’s classified decisions.
The 11-member Foreign Intelligence Surveillance Court, known as the FISA court, was once mostly focused on approving case-by-case wiretapping orders. But since major changes in legislation and greater judicial oversight of intelligence operations were instituted six years ago, it has quietly become almost a parallel Supreme Court, serving as the ultimate arbiter on surveillance issues and delivering opinions that will most likely shape intelligence practices for years to come, the officials said.
Last month, a former National Security Agency contractor, Edward J. Snowden, leaked a classified order from the FISA court, which authorized the collection of all phone-tracing data from Verizon business customers. But the court’s still-secret decisions go far beyond any single surveillance order, the officials said.
“We’ve seen a growing body of law from the court,” a former intelligence official said. “What you have is a common law that develops where the court is issuing orders involving particular types of surveillance, particular types of targets.”
In one of the court’s most important decisions, the judges have expanded the use in terrorism cases of a legal principle known as the “special needs” doctrine and carved out an exception to the Fourth Amendment’s requirement of a warrant for searches and seizures, the officials said.
“We’ve seen a growing body of law from the court,” a former intelligence official said. “What you have is a common law that develops where the court is issuing orders involving particular types of surveillance, particular types of targets.”
In one of the court’s most important decisions, the judges have expanded the use in terrorism cases of a legal principle known as the “special needs” doctrine and carved out an exception to the Fourth Amendment’s requirement of a warrant for searches and seizures, the officials said.
That legal interpretation is significant, several outside legal experts said, because it uses a relatively narrow area of the law — used to justify airport screenings, for instance, or drunken-driving checkpoints — and applies it much more broadly, in secret, to the wholesale collection of communications in pursuit of terrorism suspects. “It seems like a legal stretch,” William C. Banks, a national security law expert at Syracuse University, said in response to a description of the decision. “It’s another way of tilting the scales toward the government in its access to all this data.”
While President Obama and his intelligence advisers have spoken of the surveillance programs leaked by Mr. Snowden mainly in terms of combating terrorism, the court has also interpreted the law in ways that extend into other national security concerns. In one recent case, for instance, intelligence officials were able to get access to an e-mail attachment sent within the United States because they said they were worried that the e-mail contained a schematic drawing or a diagram possibly connected to Iran’s nuclear program.
In the past, that probably would have required a court warrant because the suspicious e-mail involved American communications. In this case, however, a little-noticed provision in a 2008 law, expanding the definition of “foreign intelligence” to include “weapons of mass destruction,” was used to justify access to the message.
The court’s use of that language has allowed intelligence officials to get wider access to data and communications that they believe may be linked to nuclear proliferation, the officials said. They added that other secret findings had eased access to data on espionage, cyberattacks and other possible threats connected to foreign intelligence.
“The definition of ‘foreign intelligence’ is very broad,” another former intelligence official said in an interview. “An espionage target, a nuclear proliferation target, that all falls within FISA, and the court has signed off on that.”
The official, like a half-dozen other current and former national security officials, discussed the court’s rulings and the general trends they have established on the condition of anonymity because they are classified. Judges on the FISA court refused to comment on the scope and volume of their decisions.
Unlike the Supreme Court, the FISA court hears from only one side in the case — the government — and its findings are almost never made public. A Court of Review is empaneled to hear appeals, but that is known to have happened only a handful of times in the court’s history, and no case has ever been taken to the Supreme Court. In fact, it is not clear in all circumstances whether Internet and phone companies that are turning over the reams of data even have the right to appear before the FISA court.
Created by Congress in 1978 as a check against wiretapping abuses by the government, the court meets in a secure, nondescript room in the federal courthouse in Washington. All of the current 11 judges, who serve seven-year terms, were appointed to the special court by Chief Justice John G. Roberts Jr., and 10 of them were nominated to the bench by Republican presidents. Most hail from districts outside the capital and come in rotating shifts to hear surveillance applications; a single judge signs most surveillance orders, which totaled nearly 1,800 last year. None of the requests from the intelligence agencies was denied, according to the court.
Beyond broader legal rulings, the judges have had to resolve questions about newer types of technology, like video conferencing, and how and when the government can get access to them, the officials said.
Beyond broader legal rulings, the judges have had to resolve questions about newer types of technology, like video conferencing, and how and when the government can get access to them, the officials said.
The judges have also had to intervene repeatedly when private Internet and phone companies, which provide much of the data to the N.S.A., have raised concerns that the government is overreaching in its demands for records or when the government itself reports that it has inadvertently collected more data than was authorized, the officials said. In such cases, the court has repeatedly ordered the N.S.A. to destroy the Internet or phone data that was improperly collected, the officials said.
The officials said one central concept connects a number of the court’s opinions. The judges have concluded that the mere collection of enormous volumes of “metadata” — facts like the time of phone calls and the numbers dialed, but not the content of conversations — does not violate the Fourth Amendment, as long as the government establishes a valid reason under national security regulations before taking the next step of actually examining the contents of an American’s communications.
This concept is rooted partly in the “special needs” provision the court has embraced. “The basic idea is that it’s O.K. to create this huge pond of data,” a third official said, “but you have to establish a reason to stick your pole in the water and start fishing.”
Under the new procedures passed by Congress in 2008 in the FISA Amendments Act, even the collection of metadata must be considered “relevant” to a terrorism investigation or other intelligence activities.
The court has indicated that while individual pieces of data may not appear “relevant” to a terrorism investigation, the total picture that the bits of data create may in fact be relevant, according to the officials with knowledge of the decisions.
Geoffrey R. Stone, a professor of constitutional law at the University of Chicago, said he was troubled by the idea that the court is creating a significant body of law without hearing from anyone outside the government, forgoing the adversarial system that is a staple of the American justice system. “That whole notion is missing in this process,” he said.
The FISA judges have bristled at criticism that they are a rubber stamp for the government, occasionally speaking out to say they apply rigor in their scrutiny of government requests. Most of the surveillance operations involve the N.S.A., an eavesdropping behemoth that has listening posts around the world. Its role in gathering intelligence within the United States has grown enormously since the Sept. 11 attacks.
Soon after, President George W. Bush, under a secret wiretapping program that circumvented the FISA court, authorized the N.S.A. to collect metadata and in some cases listen in on foreign calls to or from the United States. After a heated debate, the essential elements of the Bush program were put into law by Congress in 2007, but with greater involvement by the FISA court.
Even before the leaks by Mr. Snowden, members of Congress and civil liberties advocates had been pressing for declassifying and publicly releasing court decisions, perhaps in summary form.
Reggie B. Walton, the FISA court’s presiding judge, wrote in March that he recognized the “potential benefit of better informing the public” about the court’s decisions. But, he said, there are “serious obstacles” to doing so because of the potential for misunderstanding caused by omitting classified details.
Gen. Keith B. Alexander, the N.S.A. director, was noncommital when he was pressed at a Senate hearing in June to put out some version of the court’s decisions.
While he pledged to try to make more decisions public, he said, “I don’t want to jeopardize the security of Americans by making a mistake in saying, ‘Yes, we’re going to do all that.’ ”
Labels:
fisa,
nsa,
secret government,
surveillance
Subscribe to:
Posts (Atom)

















