 from danger room
from danger room:
One of the trickiest problems in cyber security is trying to figure who’s really behind an attack. Darpa, the Pentagon agency that created the Internet, is trying to fix that, with a new effort to develop the “cyber equivalent of fingerprints or DNA” that can identify even the best-cloaked hackers...
It’s the kind of problem Darpa will try to solve with its “Cyber Genome” project. The idea “is to produce revolutionary cyber defense and investigatory technologies for the collection, identification, characterization, and presentation of properties and relationships from collected digital artifacts of software, data, and/or users,” the agency announced late Monday. These “digital artifacts” will be collected from “traditional computers, personal digital assistants, and/or distributed information systems such as ‘cloud computers’,” as well as “from wired or wireless networks, or collected storage media. The format may include electronic documents or software (to include malicious software - malware).”
“In other words,” The Register’s Lew Page notes, “any code you write, perhaps even any document you create, might one day be traceable back to you - just as your DNA could be if found at a crime scene, and just as it used to be possible to identify radio operators even on encrypted channels by the distinctive ‘fist’ with which they operated their Morse keys. Or something like that, anyway.”
The Cyber Genome project kicks off this week with a conference in Virginia.
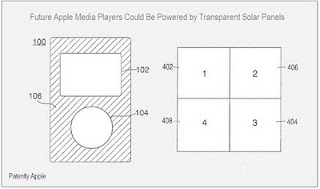 from clean technica
from clean technica:
Just on the heels of Apple’s Smart Home Energy Management System, Apple has gone and filed for a patent to reinvent their ubiquitous iPod line using solar cell technology. Transparent, or semi-transparent, solar panels would partially cover the device. If one or more of the solar cells are obstructed from light, other panels on the device will kick in to ensure a constant source of power. The device also have a standard battery in times of complete darkness. The patent expands to the iPod Shuffle, any internet-capable devices, personal organizers and computing systems. I guess that means the Apple tablet too.
china monitoring billions of texts as censorship increases from telegraph
from telegraph:
Customers of China’s two largest mobile phone networks, China Mobile and China Unicom, have had their texting service blocked after sending risqué messages, the state media claims. The disclosure comes as the country is embroiled in a dispute with Google. On Tuesday the internet giant said it could quit China because of concerns over censorship. The Global Times, a government-run newspaper, said: “Everyone seems to be under watch.” Last year, the government pledged to suppress pornography on the internet and now appears to have extended its campaign to mobile phones.aclu challenges US laptop border searchesfrom the register:
Privacy campaigners are continuing a legal challenge against random laptop border searches by US customs amid concerns there may be a racial bias in those delayed and inconvenienced by stop and search powers introduced as part of the war on terror. The ACLU also argues that searches of mobile phones by US border agents in the absence of any reason to be suspicious also pose a unwarranted invasion of privacy while delivering few tangible benefits.german govt warns against using microsoft explorerfrom bbc:
The German government has warned web users to find an alternative browser to Internet Explorer to protect security. The warning from the Federal Office for Information Security comes after Microsoft admitted IE was the weak link in recent attacks on Google's systems. Microsoft rejected the warning, saying that the risk to users was low and that the browsers' increased security setting would prevent any serious risk. However, German authorities say that even this would not make IE fully safe.fcc tells wireless mics to get off 700mhz spectrum bandfrom pcworld:
The U.S. Federal Communications Commission will prohibit hundreds of existing wireless microphone models from being used in the U.S. in five months because they operate in the 700MHz spectrum band, which was auctioned off to mobile voice and broadband carriers in 2008. The FCC prohibited electronics makers from selling existing devices that operate in the 700MHz spectrum as of Friday in an order issued the same day. Any existing devices broadcasting in the 700MHz band will have to stop operating by June 12, the FCC said. The main products affected by the ban will be wireless microphones, which have operated without FCC licenses in television spectrum for years. While many wireless microphones operate in lower spectrum bands, and will be able to continue there, the FCC has listed more than 300 models of wireless microphone and related components from 12 major manufacturers that will no longer be allowed to operate in the 700MHz band after June 12.
 from danger room
from danger room:
In Washington, “cybersecurity” is a term that’s come to have a thousand meanings, and none at all. Any crime, prank, intelligence operation, or foreign-government attack involving a computer has become a “cyber threat.” But at the Pentagon, they aren’t worried about some kid painting a Hitler moustache on Defense Secretary Robert Gates’ online portrait. They’re not even that concerned about a full-scale attack on the military’s networks – even though the modern American way of war depends so heavily on the free flow of data. In the military, there’s now broad agreement that one cyber threat trumps all others: electronic espionage, the infiltration (and possible corruption) of Defense Department networks.
Well-placed spy software not only opens a window for an adversary to look into American military operations. That window can also be used to extract information — everything from drone video feeds to ammunition requests to intelligence reports. Such an opening also gives that enemy a chance to introduce his own false data, turning American command-and-control systems against themselves. How does a soldier trust an order, if he doesn’t know who else is listening – or who gave the order in the first place? “For a sophisticated adversary, it’s to his advantage to keep your network up and running. He can learn what you know. He can cause confusion, delay your response times – and shape your actions,” says one Defense Department cyber official.
My report for the Progressive Policy Institute has more.
A few months back, the Institute’s Jim Arkedis and Will Marshall asked me to put together some thoughts on military cybersecurity. I don’t consider myself much of a policy guy. But I have hung around enough folks at the Defense Department working on the issue that I figured I’d share what I’ve found — even if that risked putting me on Nathan’s dreaded list of “reporters who heart think tanks.” Read whole paper here. And let me know what you think.
new zealand's cyber spies win new powers  from stuff.co.nz
from stuff.co.nz:
New cyber-monitoring measures have been quietly introduced giving police and Security Intelligence Service officers the power to monitor all aspects of someone's online life. The measures are the largest expansion of police and SIS surveillance capabilities for decades, and mean that all mobile calls and texts, email, internet surfing and online shopping, chatting and social networking can be monitored anywhere in New Zealand. In preparation, technicians have been installing specialist spying devices and software inside all telephone exchanges, internet companies and even fibre-optic data networks between cities and towns, providing police and spy agencies with the capability to monitor almost all communications. Police and SIS must still obtain an interception warrant naming a person or place they want to monitor but, compared to the phone taps of the past, a single warrant now covers phone, email and all internet activity. It can even monitor a person's location by detecting their mobile phone; all of this occurring almost instantaneously.nasa's kepler probe finds 5 strange new planets*facebook app maker hit with data-breach class action*
pentagon computer-network defense command delayed by congressional concerns*a decade's worth of ipv4 addresses*
canada says 'no' to yes men website*yes, in fact i do take credit!: the square adds card functionality to the iphone*
integrating skype into the family tv: net-connected mic & cam in every living room*
 from latimes
from latimes:
For a couple of precious hours Monday, the Chinese government's Web censoring system, popularly known as the Great Firewall, was lifted. Suddenly, Internet users had access to websites that had been banned for months, including YouTube, Facebook and Twitter.
Cautious excitement spread on some social-networking platforms that authorities were expanding Internet freedoms. But by the time most Chinese woke up the restrictions were back. Error messages once again flashed across computer screens for sites blocked by the nation's censorship filter.
"It seemed just like a dream," said Michael Anti, a social critic and one of hundreds who tweeted about the development on Twitter.
In many respects, it was.
Savvy computer users have found ways to scale the Great Firewall. But the vast majority of China's netizens face limits on their Internet wanderings, and that's likely to continue.
"The government isn't showing any signs of giving up on censorship," said Jonathan Zittrain, co-founder of Harvard Law School's Berkman Center for Internet and Society. "If anything, they're innovating and exploring other avenues."
 from computerworld: Reports surfacing this week say that the White House plans to put a stop to NASA's plans to return to the moon. The Orlando Sentinel, quoting an unnamed White House source, reported yesterday that President Barack Obama is looking to push the space agency in a new direction.
from computerworld: Reports surfacing this week say that the White House plans to put a stop to NASA's plans to return to the moon. The Orlando Sentinel, quoting an unnamed White House source, reported yesterday that President Barack Obama is looking to push the space agency in a new direction.









