google/cia invest in 'future' of pre-crime from danger room
from danger room:
The investment arms of the CIA and Google are both backing a company that monitors the web in real time - and says it uses that information to predict the future.
The company is called Recorded Future, and it scours tens of thousands of websites, blogs and Twitter accounts to find the relationships between people, organizations, actions and incidents - both present and still-to-come. In a white paper, the company says its temporal analytics engine “goes beyond search” by “looking at the ‘invisible links’ between documents that talk about the same, or related, entities and events.”
The idea is to figure out for each incident who was involved, where it happened and when it might go down. Recorded Future then plots that chatter, showing online “momentum” for any given event.
“The cool thing is, you can actually predict the curve, in many cases,” says company CEO Christopher Ahlberg, a former Swedish Army Ranger with a PhD in computer science.
Which naturally makes the 16-person Cambridge, Massachusetts, firm attractive to Google Ventures, the search giant’s investment division, and to In-Q-Tel, which handles similar duties for the CIA and the wider intelligence community.
It’s not the very first time Google has done business with America’s spy agencies. Long before it reportedly enlisted the help of the National Security Agency to secure its networks, Google sold equipment to the secret signals-intelligence group. In-Q-Tel backed the mapping firm Keyhole, which was bought by Google in 2004 — and then became the backbone for Google Earth.
This appears to be the first time, however, that the intelligence community and Google have funded the same startup, at the same time. No one is accusing Google of directly collaborating with the CIA. But the investments are bound to be fodder for critics of Google, who already see the search giant as overly cozy with the U.S. government, and worry that the company is starting to forget its “don’t be evil” mantra.
 from threat level
from threat level:
Federal regulators lifted a cloud of uncertainty when they announced it was lawful to hack or “jailbreak” an iPhone, declaring Monday there was “no basis for copyright law to assist Apple in protecting its restrictive business model.”
Jailbreaking is hacking the phone’s OS to allow consumers to run any app on the phone they choose, including applications not authorized by Apple.
The Electronic Frontier Foundation asked regulators 19 months ago to add jailbreaking to a list of explicit exemptions to the Digital Millennium Copyright Act’s anti-circumvention provisions.
At stake for Apple is the very closed business model the company has enjoyed since 2007, when the iPhone debuted. Apple says it’s unlawful to jailbreak, (.pdf) but has not taken legal action against the millions who have jailbroken their phones and used the underground app store Cydia.
Apple maintains that its closed marketplace is what made the success of the iPhone possible, and sold more than three billion apps. Apple also told regulators that the nation’s cellphone networks could suffer “potentially catastrophic” cyberattacks by iPhone-wielding hackers at home and abroad (.pdf) if iPhone owners are permitted to legally jailbreak their shiny wireless devices.
 from daily mail
from daily mail:
A Chinese airport was closed after this mysterious object was spotted in the sky. Arcing over Zhejiang's provincial capital Hangzhou, the UFO appeared to glow with an eerie white light and left a bright trail in its wake. Xiaoshan Airport was closed after the UFO was detected at around 9 pm and dozens of flights had to be diverted. Stunned witnesses reported seeing a comet-like fireball in the sky and a number of local residents took photos of the strange ball of light.
A local bus driver, giving his name only as Yu, said he had seen a strange glowing object in the sky late on Wednesday afternoon. 'The thing suddenly ran westwards fast, like it was escaping from something,' he said. Inbound flights were diverted to nearby airports while outbound flights were delayed for three to four hours. Some Chinese experts claimed that the strange sight was actually debris from a US intercontinental ballistic missile. Chinese officials later said that they knew what the object had been but were unable to make it public because there was a 'military connection.' An official statement is expected later today.
"be sure to drink your ovaltine fight the net" from danger room
from danger room:
The U.S. military’s new Cyber Command is headquartered at Ft. Meade, Maryland, one of the military’s most secretive and secure facilities. Its mission is largely opaque, even inside the armed forces. But the there’s another mystery surrounding the emerging unit. It’s embedded in the Cyber Command logo.
On the logo’s inner gold ring is a code: 9ec4c12949a4f3147
4f299058ce2b22a
“It is not just random numbers and does ‘decode’ to something specific,” a Cyber Command source tells Danger Room. “I believe it is specifically detailed in the official heraldry for the unit symbol... While there a few different proposals during the design phase, in the end the choice was obvious and something necessary for every military unit,” the source adds. “The mission.”
With that hint in hand, go crack this code open. E-mail us your best guess, or leave it in the comments below. Our Cyber Command source will confirm the right answer. And the first person to get it gets his/her choice of a Danger Room T-shirt or a ticket to the International Spy Museum.update: code cracked! cybercom logo's mystery solvedfrom danger room:
Okay, maybe it wasn’t that much of a mystery. In fact, it took a little more than three hours your Danger Room reader jemelehill to figure out the odd string of letters and numbers in the logo of the U.S. military’s new Cyber Command. Turns out, it’s the new unit’s mission statement, translated into 32 digits with the md5 cryptographic hash:USCYBERCOM plans, coordinates, integrates, synchronizes, and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full-spectrum military cyberspace operations in order to enable actions in all domains, ensure freedom of action in cyberspace for the U.S. and its allies, and deny the same to adversaries.
Eventually, other commenters figured it out (especially after jemelehill’s solution made it to all the databases of cracked hashes). But that didn’t stop folks from offering their own, shall we say, creative guesses, in order to win one of two coveted prizes: a Danger Room t-shirt or a ticket to the International Spy Museum.* “If you can read this, send your resume to jobs@nsa.gov.”
* “I’m sorry, Dave. I’m afraid I can’t do that.”
* “If the intelligence community is a family, think of us as the uncle no one talks about.”
* “Darmok and Jalad at Tanagra”
* “In God We Trust All Others We Monitor”
* “Why do people keep posting the wrong answers when someone solved it like 20 comments ago?”
Yahoo News, the Associated Press, Agence Presse France, Slashdot, El Reg, and the websites of the Washington Post and the L.A. Times all joined in the fun. The hubub even provoked this reponse from an official Defense Department blog:I cracked the code, but you can keep my t-shirt.
 from washington post
from washington post:
An Army intelligence analyst has been charged in connection with the leak of a controversial video of a U.S. helicopter strike and the transfer of more than 50 classified State Department cables, the military said Tuesday.
Pfc. Bradley Manning, 22, was detained in Kuwait in May after Wikileaks, a whistleblower Web site, released the video, which it titled "Collateral Murder." The footage, taken by cameras on U.S. Apache helicopters, shows several civilians, including two Reuters news agency employees, being killed in a U.S. strike in July 2007.
Manning faces two charges under the Uniform Code of Military Justice. The first encompasses four counts of violating Army regulations by transferring classified information to his personal computer between November and May and adding unauthorized software to a classified computer system. The second comprises eight counts of violating federal laws governing the handling of classified information.
Among the materials Manning is accused of transmitting to "a person not entitled to receive them" are the video and more than 50 classified diplomatic cables. According to the charge sheet, he allegedly downloaded more than 150,000 cables in all.
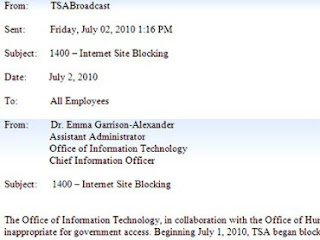 from cbsnews
from cbsnews:
The Transportation Security Administration (TSA) is blocking certain websites from the federal agency's computers, including halting access by staffers to any Internet pages that contain a "controversial opinion," according to an internal email obtained by CBS News. The email was sent to all TSA employees from the Office of Information Technology on Friday afternoon. It states that as of July 1, TSA employees will no longer be allowed to access five categories of websites that have been deemed "inappropriate for government access." The categories include:
• Chat/Messaging
• Controversial opinion
• Criminal activity
• Extreme violence (including cartoon violence) and gruesome content
• Gaming
The email does not specify how the TSA will determine if a website expresses a "controversial opinion." There is also no explanation as to why controversial opinions are being blocked, although the email stated that some of the restricted websites violate the Employee Responsibilities and Conduct policy. The TSA did not return calls seeking comment by publication time.update: tsa reverses 'controversial opinion' web policy
 hackers shut down eu carbon-trading website*
hackers shut down eu carbon-trading website* 












